
During the 76 days since Emotet’s return, researchers have observed activity reminiscent of past Emotet campaigns, like high message volumes and global distribution.
Emotet uses a variety of lure themes, some of which occasionally leverage current events or news items, like COVID-19 or Greta Thunberg. While TA542, the actor behind Emotet, has sent messages to local, state, and other government recipients, historically they have not directly leveraged political themes in their messaging.
On October 1, 2020, we observed thousands of Emotet email messages with the subject “Team Blue Take Action” sent to hundreds of organizations in the US. The message body is taken directly from a page on the Democratic National Committee’s website, with the addition of a line requesting that the recipient open the attached document.
Sherrod DeGrippo, Senior Director, Threat Research and Detection at Proofpoint:
“Proofpoint prevented thousands of malicious emails from hitting unsuspecting voters nationwide—and it’s essential that everyone is aware that threat actors are actively working to impersonate trusted sources this election season.
Emotet is one of the world’s most disruptive threats and their quick use of DNC-themed emails following this week’s presidential debate demonstrates just how swiftly threat actors can tailor their email lures to focus on prominent events. To avoid impersonation attempts this election cycle approaches all unsolicited emails with extreme caution especially if they ask you to take urgent action. Do not open email attachments or click on emailed links and be sure to deeply examine any and all digital communication surrounding the election to verify authenticity and reduce risk.”
Attached is a malicious Word document, “Team Blue Take Action.” The Word doc contains macros which, if enabled by the intended recipient, will download and install Emotet. The current second-stage payload we’ve observed following Emotet is Qbot “partner01” and The Trick “morXXX” (e.g., “mor125”).
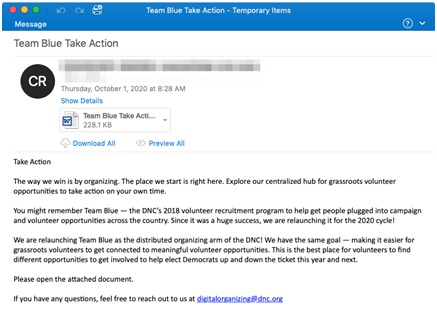
Figure 1: ”Team Blue Take Action” lure containing malicious Word doc attachment
Sample of additional related subjects observed includes:
Sample of additional related filenames observed includes:
The shift to using politically-themed lures comes days after the first of several 2020 US Presidential debates. The debate received widespread media coverage, and as Election Day draws nearer, many voters are likely feeling compelled to volunteer for political causes or for the election in some way. However, it’s unlikely that this shift is driven by any specific political ideology. Like earlier use of COVID-19 or Greta Thunberg lure themes, TA542 is attempting to reach as many intended recipients as possible by capitalizing on a popular topic.
