ESET Research has uncovered a new banking trojan that has been targeting corporate users in Brazil since at least 2019 across many sectors, including engineering, healthcare, retail, manufacturing, finance, transportation, and governmental institutions. ESET dubbed the new threat Janeleiro.
It attempts to deceive its victims with pop-up windows designed to look like the websites of some of the largest banks in Brazil. After that, it tricks the malware’s victims into entering their banking credentials and personal information. It is capable of controlling on-screen windows, collecting information about them, killing chrome.exe (Google Chrome), screen capture, as well as keylogging control keys, mouse movements, and it can hijack the clipboard to change bitcoin addresses with those of the criminals in real time.
Throughout 2020-2021, ESET has been running a series of investigations on prominent banking trojan malware families targeting Latin America. Janeleiro follows the same blueprint for its core implementation as many other malware families that target Brazil. However, it sets itself apart from those families in several ways, such as is coding language. Following the blueprint, banking trojans in Brazil are all coded in the same programming language, Delphi, Janeleiro is the first one seen in Brazil to be coded in .NET. Other distinguishing features include: no obfuscation, no custom encryption, and no defenses against security software.
The majority of Janeleiro’s commands are for the control of windows, the mouse and keyboard, and its fake pop-up windows. “The nature of a Janeleiro attack is not characterized by its automation capabilities, but rather by the hands-on approach: in many cases, the operator must adjust the pop-up windows via commands executed in real time,” says ESET researcher Facundo Muñoz, who discovered Janeleiro.
“It appears that banking trojan was under development as far back as 2018, and in 2020, improved its command processing to give the operator better control during the attack,” adds Muñoz, who continues: “The experimental nature of Janeleiro coming back and forth between different versions reveals a threat actor who is still trying to find the right way to manage his tools, but is no less experienced in following the unique blueprint of many malware families in Latin America.”
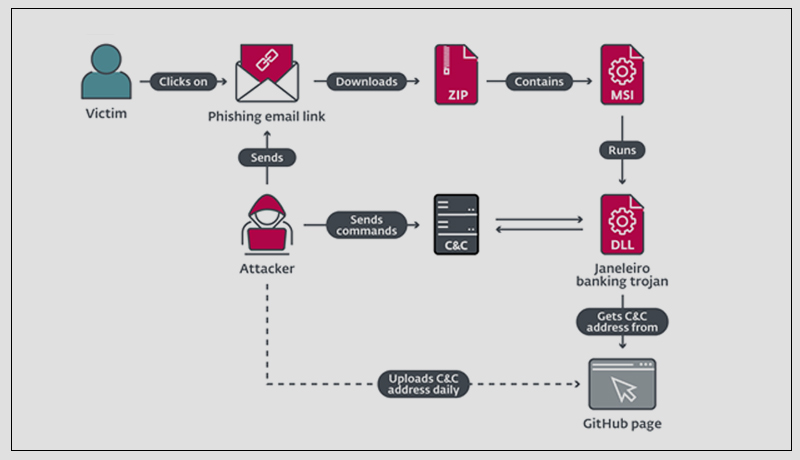
Interestingly, this threat actor feels comfortable using the GitHub repository website to store its modules, administrating its organization page, and uploading new repositories every day where it stores the files with the lists of its C&C servers that the trojans retrieve to connect to their operators. When one of the banking-related keywords is found on the victim’s machine, it immediately attempts to retrieve the addresses of its C&C servers from GitHub and connects to them. These fake pop-up windows are dynamically created on demand and controlled by the attacker via commands. ESET has notified GitHub of this activity, but at the time of writing, no action has been taken against the organization page nor the user account.
For more technical details about Janeleiro, read the blogpost “Janeleiro, the time traveler: A new old banking trojan in Brazil” on WeLiveSecurity. Make sure to follow ESET Research on Twitter for the latest news from ESET Research.
Janeleiro attack overview (simplified)