
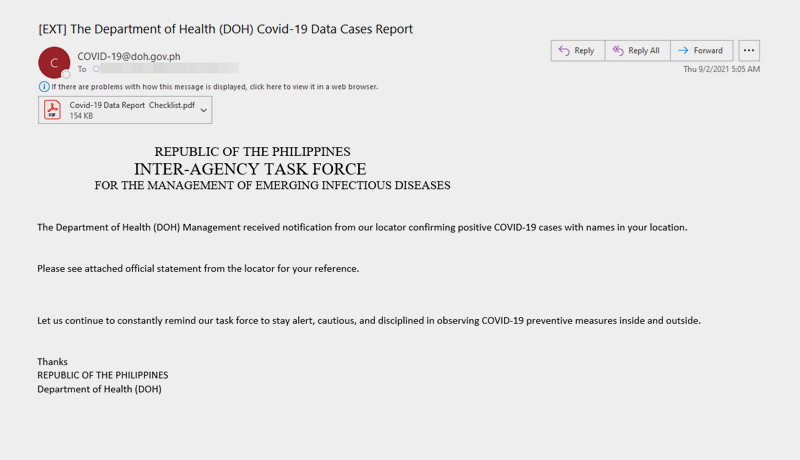
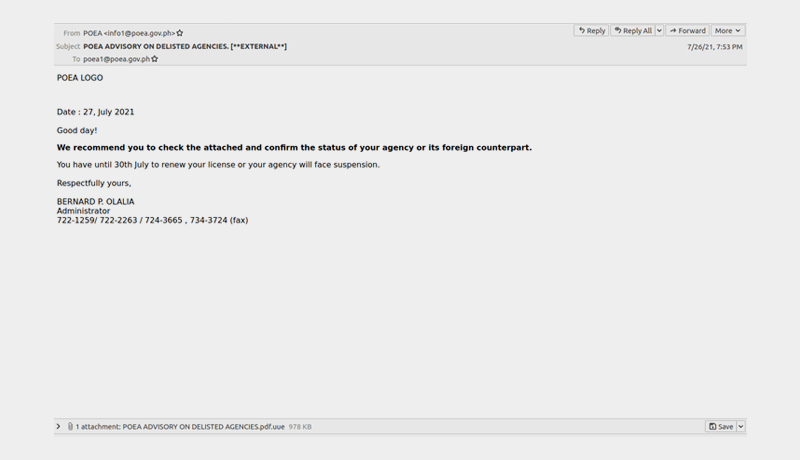
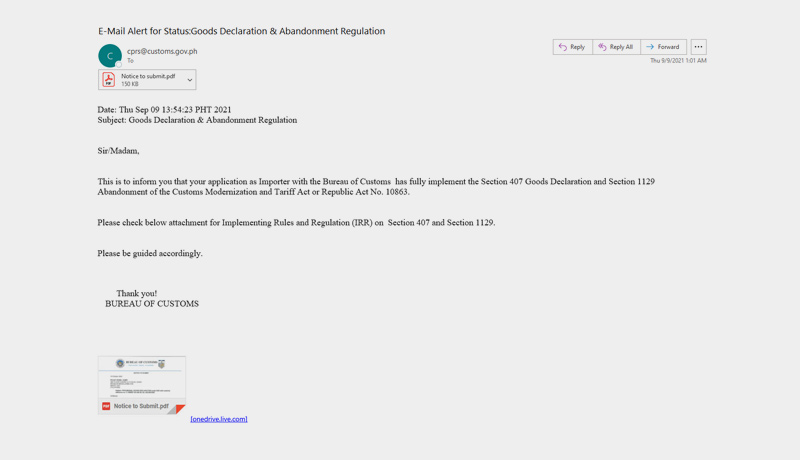
Proofpoint, Inc. has discovered TA2722, also known as the Balikbayan Foxes, a new and highly active cybercriminal threat actor. Several Philippine government institutions, including the Department of Health, the Philippine Overseas Employment Administration (POEA), and the Bureau of Customs, were impersonated in a series of campaigns in 2021. Other linked campaigns posed as the Saudi Arabian (KSA) embassy in Manila and DHL Philippines.
The communications were aimed towards a wide range of industries in North America, Europe, and Southeast Asia, with shipping, logistics, manufacturing, business services, pharmaceuticals, energy, and finance among the most prominent.
Based on a consistent pattern of spoofing email addresses and distributing lures designed to impersonate official bodies, Proofpoint believes this actor is targeting groups directly or indirectly involved with the Philippine government. At ports of call, for example, shipping, transportation, and logistics companies would frequently interact with customs officers. Furthermore, manufacturing and energy businesses support and maintain significant supply chain operations, almost certainly necessitating communication with labor and customs bodies.
Remcos or NanoCore remote access trojans were delivered in all of the campaigns (RATs). Information gathering, data theft activities, monitoring, and control of infected systems are all common uses for Remcos and NanoCore. The sender emails were reused for a long time, even though the malware’s related infrastructure changed over time.
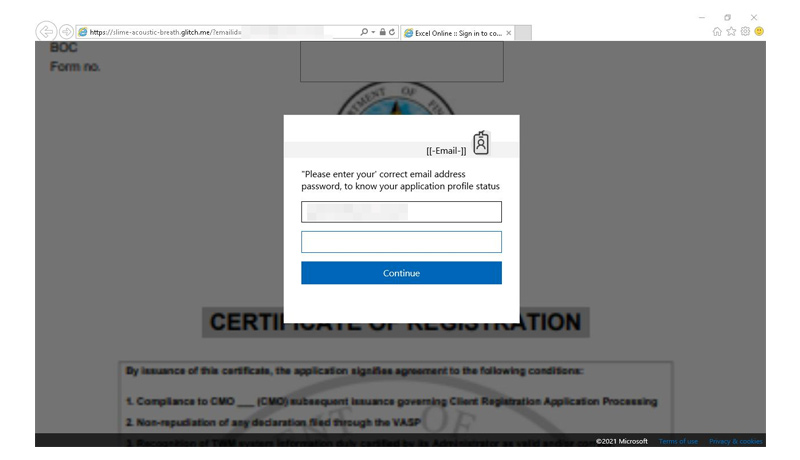
Multiple threat distribution mechanisms were included in the message lures, including OneDrive URLs linking to RAR files with embedded UUE files, PDF email attachments with an embedded OneDrive link or other malicious URL leading to compressed executables (.iso files) that download and run malware, and compressed MS Excel documents with macros that, if enabled, download malware.

TA2722 is a highly active threat actor that targets a range of organizations in Southeast Asia, Europe, and North America using Philippine government themes. This threat actor is most likely attempting to acquire remote access to target systems, which might be used for data collection, malware installation, or business email compromise (BEC) activity.
Multiple advisories were issued by Philippine government institutions in 2020, warning users of activities related to lures with themes like COVID-19 infection information in the Philippines and POEA labour information.
