
ESET researchers discovered a previously unknown macOS backdoor that spies on users of compromised Macs and only communicates with its operators via public cloud storage services.
The capabilities of CloudMensis, as named by ESET, clearly show that the operators’ intent is to gather information from the victims’ Macs by exfiltrating documents and keystrokes, listing email messages and attachments, listing files from removable storage, and screen captures. CloudMensis is a threat to Mac users, but its limited distribution indicates that it is part of a targeted operation.
According to ESET Research, operators of this malware family deploy CloudMensis to specific targets of interest to them. The use of vulnerabilities to circumvent macOS mitigations indicates that malware operators are actively attempting to maximize the success of their spying operations. At the same time, no unknown vulnerabilities (zero days) were discovered to be used by this group during our investigation. As a result, running an up-to-date Mac is advised to avoid, at the very least, the mitigation bypasses. “We still do not know how CloudMensis is initially distributed and who the targets are. The general quality of the code and lack of obfuscation shows the authors may not be very familiar with Mac development and are not so advanced. Nonetheless, a lot of
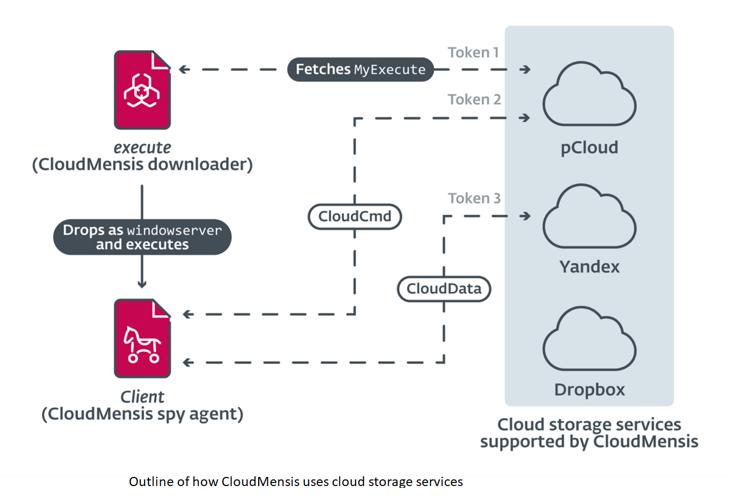
resources were put into making CloudMensis a powerful spying tool and a menace to potential targets,” explains ESET researcher Marc-Etienne Léveillé, who analyzed CloudMensis. After gaining code execution and administrative privileges, CloudMensis executes a first-stage malware that downloads a more feature-rich second stage from a cloud storage service. This second stage is a much larger component, jam-packed with features for gathering data from the compromised Mac. The attackers’ clear goal here is to steal documents, screenshots, email attachments, and other sensitive data. In total, 39 commands are currently available.
CloudMensis uses cloud storage to receive commands from its operators as well as to exfiltrate files. It works with three providers: pCloud, Yandex Disk, and Dropbox. Authentication tokens for pCloud and Yandex Disk are included in the configuration included in the analyzed sample. The metadata from the cloud storage services used reveals interesting details about the operation, such as the fact that it began transmitting commands to the bots on February 4, 2022.
Apple has recently acknowledged the presence of spyware targeting users of its products and is testing Lockdown Mode on iOS, iPadOS, and macOS, which disables features commonly used to gain code execution and deploy malware.
