
To understand the global impact of COVID-19 on the security posture of organizations, the Unit 42 cloud threat intelligence team analyzed data from hundreds of cloud accounts around the world between October 2019 and February 2021 (before and after the onset of the pandemic). Our research indicates that cloud security incidents increased by an astounding 188% in the second quarter of 2020 (April to June). We found that, although organizations quickly moved more workloads to the cloud in response to the pandemic, they struggled many months later to automate cloud security and mitigate cloud risks. While infrastructure as code (IaC) offers DevOps and security teams a predictable way to enforce security standards, this powerful capability continues to go unharnessed. This report details the scope of COVID-19’s impact on the cloud threat landscape and explains which types of risks are most prevalent in specific geographies and industries. It also identifies actionable steps organizations can take to reduce the security risks associated with their cloud workloads.
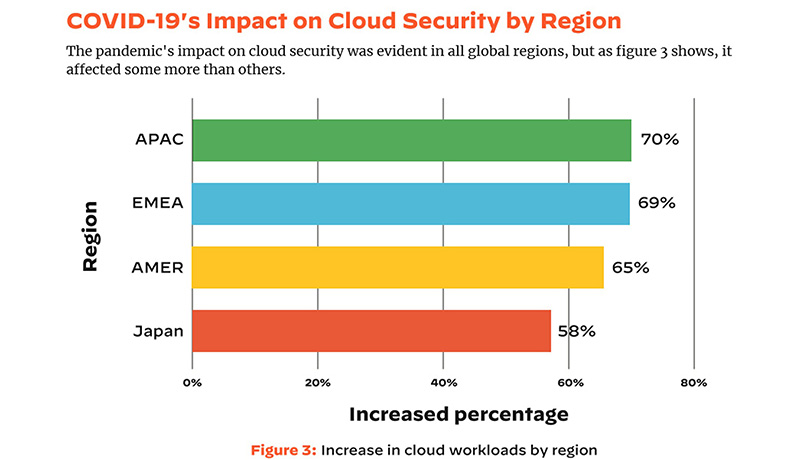
Organizations experienced large expansions in the size of cloud workload deployments following the onset of the pandemic, but they also suffered an uptick in cloud security incidents. Of note, cloud security incidents for the retail, manufacturing, and government industries rose by 402%, 230%, and 205%, respectively. This trend is not surprising; these same industries were among those facing the greatest pressures to adapt and scale in the face of the pandemic—retailers for basic necessities, and manufacturing and government for COVID-19 supplies and aid.
Industries that play crucial roles in combating the pandemic are struggling to secure their cloud workloads, underscoring the danger of underinvesting in cloud security. Such spikes in cloud security incidents make clear that, although the cloud allows businesses to quickly expand their remote work capabilities, automated security controls around DevOps and continuous integration/continuous delivery (CI/CD) pipelines often lag behind this rapid movement.
While the pandemic raged, cryptocurrencies such as Bitcoin (BTC), Ethereum (ETH), and Monero (XMR) grew in popularity and market value. Despite this, cryptojacking is trending down: from December 2020 through February 2021, only 17% of organizations with cloud infrastructure showed signs of this activity, compared to 23% from July through September 2020. This is the first recorded drop since Unit 42 began tracking cryptojacking trends in 2018. Organizations appear to be blocking cryptojacking more proactively. This can be done effectively through workload runtime protections that mitigate an attackers’ ability to run malicious cryptomining software undetected in enterprise cloud environments.
Our findings indicate that 30% of organizations expose some sensitive content to the internet, such as personally identifiable information (PII), intellectual property, and healthcare and financial data. Anyone who knows or can guess the URLs can access this data. When this data is exposed directly to the internet, organizations face significant risks associated with unauthorized access and regulatory compliance violations. This degree of exposure suggests that organizations continue to struggle to enforce proper access controls for the hundreds of data storage buckets that may operate in the cloud, especially when those buckets are spread across multiple cloud providers and accounts.
