
Delinea, a provider of Privileged Access Management (PAM) solutions for seamless security, announced the results of a global survey of 2,100 IT Security Decision Makers (ITSDMs), which revealed that 60% of respondents believe their overall security strategy is falling behind (20%), treading water (13%), or simply running to keep up (27 percent ). The study, which was conducted in over 20 countries, polled people’s attitudes toward identity security and the protection of privileged identities.
The report also highlights discrepancies between security strategies’ perceived and actual effectiveness. While 40% of respondents believe they have the right strategy in place, 84% of organizations reported an identity-related breach or an attack using stolen credentials in the previous year and a half.

Respondents from the UAE and KSA are more skeptical of their security strategies than respondents from other countries, with more than half (53 percent) believing their overall security strategy is ‘in the doldrums’ and requires a re-energisation of cyber security across the organization, and only 16 percent believing they can keep pace with the threat landscape. Simultaneously, an astounding 91 percent reported an identity-related breach or an attack using stolen credentials in the previous year and a half.

Identity security is a priority, yet board buy-in is critical
Many organizations, it appears, are eager to make a difference, particularly when it comes to identity protection. In line with the global findings, 94 percent of respondents in the UAE and Saudi Arabia (90 percent globally) say their organizations fully recognize the importance of identity security in enabling them to achieve their business goals, and 86 percent say it is one of the most important security priorities for the next 12 months.
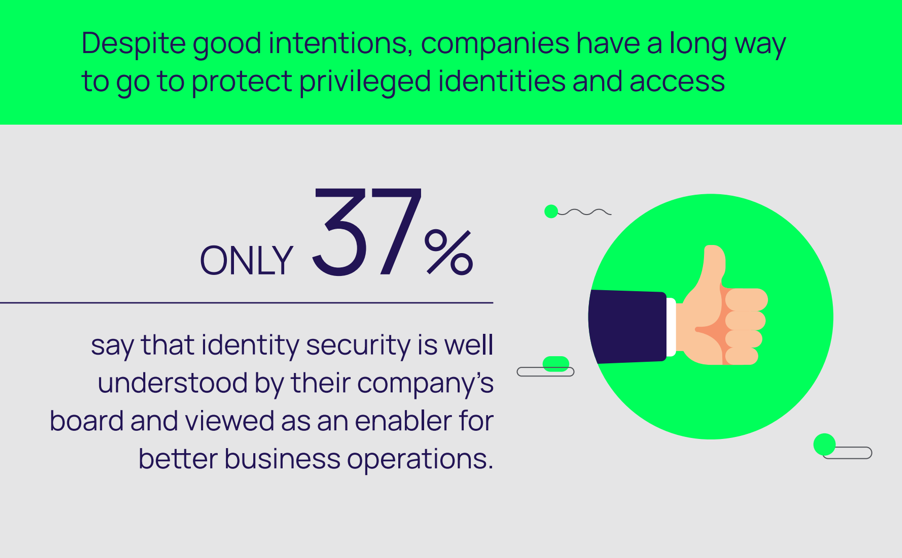
However, 85 percent of UAE and Saudi respondents (75 percent globally) believe they will fall short of protecting privileged identities because they will not receive the necessary support. This is largely due to a lack of budget and executive alignment, with 68 percent of regional respondents reporting that their company’s board of directors still does not fully understand identity security and its role in enabling better business operations.
“While the importance of identity security is acknowledged by business leaders, most Middle East security teams will not receive the backing and budget they need to put vital security controls and solutions in place to reduce major risks,” comments Joseph Carson, Chief Security Scientist and Advisory CISO at Delinea. “This means that the majority of organisations will continue to fall short of protecting privileges, leaving them vulnerable to cybercriminals looking to discover privileged accounts and abuse them.”
Lack of policies puts machine identities at great risk
According to the findings, despite good intentions, companies have a long way to go in protecting privileged identities and access. Less than one-third (31%) of the regional organizations surveyed have ongoing security policies and processes for privileged access management, such as password rotation or approvals, time-based or context-based security, or privileged behavior monitoring, such as recording and auditing. Worryingly, half of all UAE and Saudi organizations polled allow privileged users to access sensitive systems and data without requiring multi-factor authentication (MFA).
Another dangerous oversight is revealed by the report. Humans, such as domain and local administrators, are examples of privileged identities, as are non-humans, such as service accounts, application accounts, code, and other types of machine identities that automatically connect and share privileged information. However, only 52% of UAE and KSA organizations manage and secure machine identities, leaving a troubling proportion exposed and vulnerable to attack.
Carson added, “Cyber criminals look for the weakest link and overlooking ‘non-human’ identities—particularly when these are growing at a faster pace than human users—greatly increases the risk of privilege-based identity attacks. When attackers target machine and application identities they can easily hide, moving around the network to determine the best place to strike and cause the most damage. Organisations need to ensure machine identities are included in their security strategies and follow best practices when it comes to protecting all their IT ‘superuser‘ accounts which, if compromised, could bring the entire business to a halt.”
