
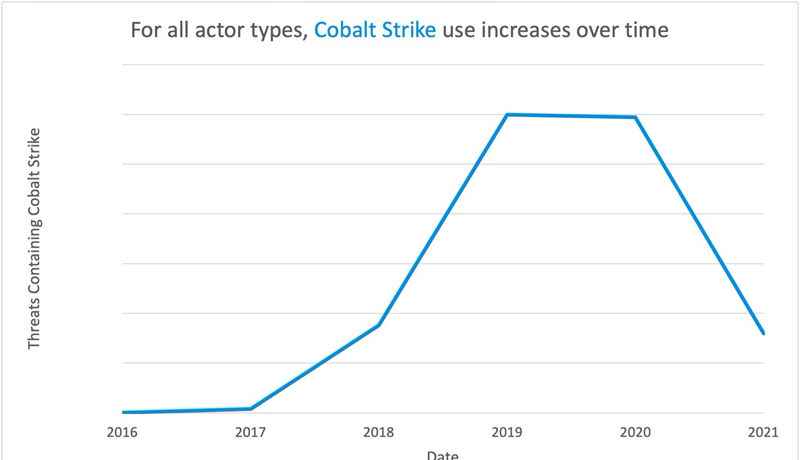
Cobalt Strike: Favorite tool from Advanced Persistent Threat(APT) to crimeware. In 2021, Cobalt Strike is appearing in Proofpoint threat data more frequently than ever. Cobalt Strike is a legitimate security tool used by penetration testers to emulate threat actor activity in a network. However, it is also increasingly used by malicious actors – Proofpoint saw a 161 percent increase in threat actor use of the tool from 2019 to 2020. This aligns with observations from other security firms as more threat actors adopt hacking tools in their operations.
When mapped to the MITRE ATT&CK framework, Proofpoint’s visibility into the attack chain focuses on Initial Access, Execution, and Persistence mechanisms. Based on our data, Proofpoint assesses with high confidence that Cobalt Strike is becoming increasingly popular among threat actors as an initial access payload, not just a second-stage tool threat actors use once access is achieved, with criminal threat actors making up the bulk of attributed Cobalt Strike campaigns in 2020.
In December 2020, the world learned about an expansive and effective espionage campaign that successfully backdoored the popular network monitoring software SolarWinds. Investigators revealed toolsused by the threat actors included Cobalt Strike Beacon. This high-profile activity was part of a clever attack chain enabling advanced threat actors to surreptitiously compromise a relatively small number of victims.
Historically, Cobalt Strike use in malicious operations was largely associated with well-resourced threat actors, including large cybercrime operators like TA3546(also known as FIN7), and advanced persistent threat (APT) groups such as TA423 (also known as Leviathan or APT40).
In March 2020, a cracked version of Cobalt Strike 4.0 was released and made available to threat actors.
Cobalt Strike is used by a diverse array of threat actors, and while it is not unusual for cybercriminal and APT actors to leverage similar tooling in their campaigns, Cobalt Strike is unique in that its built-in capabilities enable it to be quickly deployed and operationalized regardless of actor sophistication or access to human or financial resources.
Cobalt Strike is also session-based — that is, if threat actors can access a host and complete an operation without needing to establish ongoing persistence, there will not be remaining artifacts on the host after it is no longer running in-memory. In essence: they can hit it and forget it.
Cobalt Strike is also appealing to threat actors for its inherent obfuscation. Attribution gets more difficult if everyone is using the same tool. If an organization has a red team actively making use of it, it is possible malicious traffic could be mistaken as legitimate. The software’s ease of use can improve the capabilities of less sophisticated actors. For sophisticated actors, why spend development cycles on something new when you already have a great tool for the job?
Cobalt Strike is a popular tool for everything from strategic compromises to noisy, widespread campaigns. there are different types of threat actors leveraging Cobalt Strike, including TA800, TA547 and TA415
There are dozens of threat actors using Cobalt Strike, however those use different lure themes, threat types, droppers, and payloads. For example, the earliest Cobalt Strike campaigns distributed email threats with malicious document attachments to distribute the malware, but campaigns distributing malicious URLs directly in the email body have overtaken attachments as the more frequently utilized threat type.
While instances of Cobalt Strike being sent directly as an initial payload have dramatically increased, deployment as a second stage payload remains popular. Cobalt Strike has been observed in a variety of attack chains alongside malware such as The Trick, BazaLoader, Ursnif, IcedID, and many more popular loaders.
In addition to network discovery and credential dumping, Cobalt Strike Beacon also has the capability to elevate privileges, load and execute additional tools, and to inject these functions into existing running host processes to attempt to avoid detection.
Proofpoint anticipates Cobalt Strike will continue to be a commonly used tool in threat actor toolsets. According to internal data, tens of thousands of organizations have already been targeted with Cobalt Strike, based on observed campaigns. We expect this number to increase in 2021.
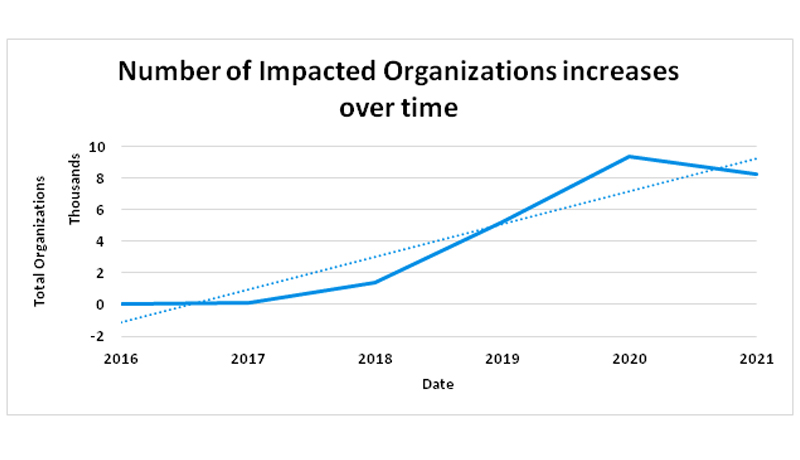
Figure 4: Number of customers targeted by threats using Cobalt Strike
Cobalt Strike is a useful tool, for legitimate security researchers and threat actors alike. Its malleability coupled with its usability makes it a robust and effective tool for siphoning data, moving laterally, and loading additional malware payloads.
Apart from Cobalt Strike, there are other red team tools, including Mythic, Meterpreter, and the Veil Framework.
The use of publicly available tooling aligns with a broader trend observed by Proofpoint: Threat actors are using as many legitimate tools as possible, including executing Windows processes like PowerShell and WMI; injecting malicious code into legitimate binaries; and frequently using allowable services like Dropbox, Google Drive, SendGrid, and Constant Contact to host and distribute malware.