23 December 2024, Mon |
1:11 PM

Group-IB has released its second annual threat evolution guide, “Ransomware Uncovered 2021/2022.”
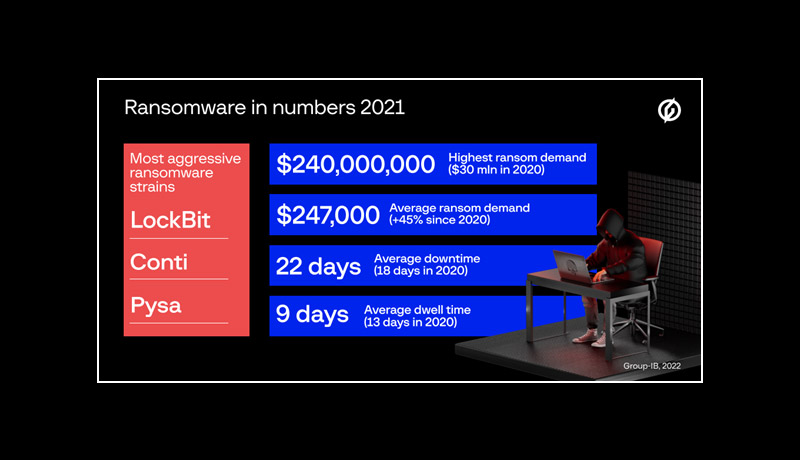
According to the findings of the second edition of the report, the ransomware empire’s winning streak continued, with the average ransom demand increasing by 45 percent to $247,000 in 2021. Since 2020, ransomware gangs have become far more greedy. Hive from MediaMarkt demanded a record-breaking ransom of $240 million ($30 million in 2020). Hive and Grief, another 2021 newcomer to the Big Game Hunting, quickly rose to the top ten gangs based on the number of victims posted on dedicated leak sites (DLS).
According to the report, between Q1 2021 and Q1 2022, data from 147 MEA companies was uploaded on ransomware DLS. In the GCC region, 17 UAE companies had their data posted on DLS, followed by Saudi Arabia (15 victim-companies), Kuwait (6 victims), and Qatar (5 victims).
The new report summarizes the most recent tactics, techniques, and procedures (TTPs) of ransomware threat actors observed by Group-Digital IB’s Forensics and Incident Response (DFIR) team across all geographic locations. The report examines ransomware DLS in addition to the analysis of more than 700 attacks investigated as part of Group-own IB’s incident response engagements and cyber threat intelligence activity in 2021.
Over the last three years, human-operated ransomware attacks have maintained a solid lead in the global cyber threat landscape. The rise of initial access brokers, as described in Group-Hi-Tech IB’s Crime Trends report, and the expansion of Ransomware-as-a-Service (RaaS) programs have become the two main driving forces behind the ongoing expansion of ransomware operations. RaaS enabled low-skilled cybercriminals to enter the game, ultimately increasing the victim count.
Based on an analysis of over 700 attacks in 2021, Group-IB DFIR experts estimated that ransom demand would average $247,000 in 2021, up 45% from 2020. Ransomware has become more sophisticated, as evidenced by the victim’s downtime, which has increased from 18 days in 2020 to 22 days in 2021.
RaaS programs began offering their affiliates custom tools for data exfiltration in order to simplify and streamline operations. As a result, the double extortion technique became even more common – sensitive victim data was exfiltrated as a leverage to obtain the ransom in 63 percent of cases examined by the Group-IB DFIR team. Ransomware gangs posted data belonging to over 3,500 victims on DLS between Q1’2021 and Q1’2022. The majority of companies whose data was posted on DLS by ransomware operators in 2021 were based in the United States (1,655), Canada (176), and the United Kingdom (168), with the manufacturing (322), real estate (305), and professional services (256) industries being the most affected.
According to the report, between Q1 2021 and Q1 2022, data from 147 MEA companies was uploaded on ransomware DLS. In the GCC region, ransomware threat actors posted data from 17 UAE companies on DLS, followed by 15 Saudi companies, 6 Kuwait companies, and 5 Qatar companies.
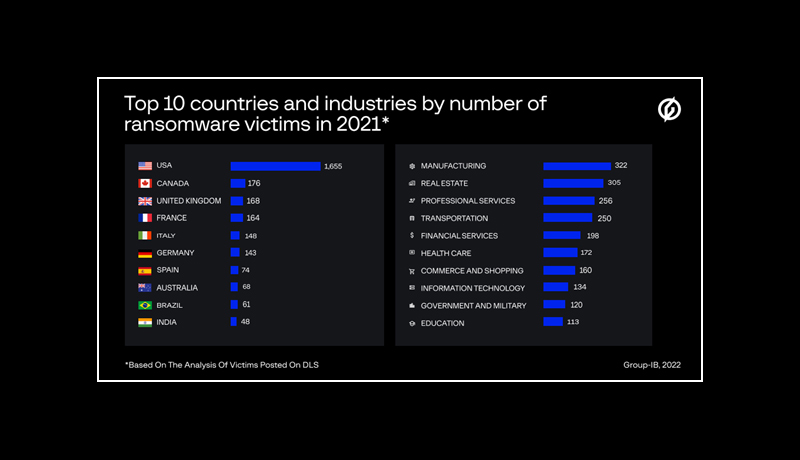
Lockbit, Conti, and Pysa turned out to be the most aggressive gangs with 670, 640, and 186 victims uploaded on DLS respectively.
In the UAE specifically, the most active ransomware gang in 2021 was Lockbit with 6 companies posted on DLS between Q1 2021 and Q1 2022, followed by Prometheus (2), 54bb47h (1), Avaddon (1), Darkside (1) and others. Industry-wise, most of the affected companies in the UAE were from the real estate sector (3).
Exploitation of public-facing RDP servers once again became the most common way to gain an initial foothold in the target network in 2021 – 47% of all the attacks investigated by Group-IB DFIR experts started with compromising an external remote service.
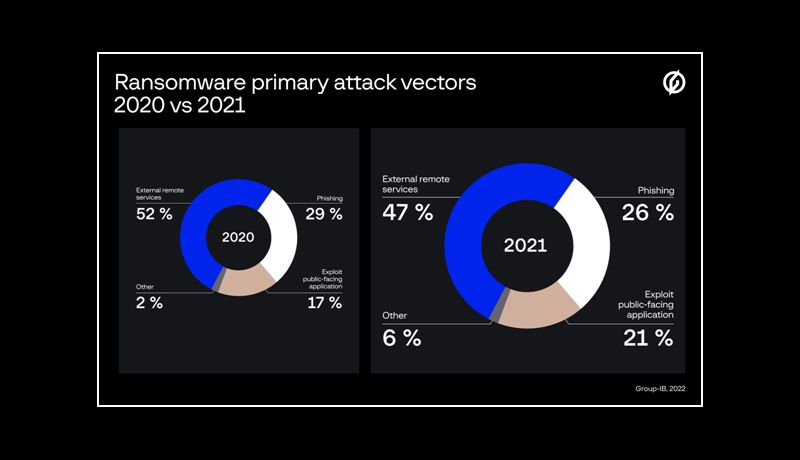
Spear phishing emails containing commodity malware remained in second place (26 percent ). Commodity malware used in the early stages has grown in popularity among ransomware actors. However, attribution of ransomware attacks became increasingly complicated in 2021 due to the widespread use of bots such as Emotet, Qakbot, and IcedID by various threat actors, in contrast to 2020, when certain commodity malware families had strong ties to specific ransomware gangs.
Some ransomware gangs were seen taking very unusual approaches, such as using zero-day vulnerabilities to attack Kaseya’s clients. Vishing was used to distribute BazarLoader, which was used in Ryuk operations (voice phishing). Phishing emails allegedly contained information about “paid subscriptions” that could be canceled over the phone.
“Given multiple rebrands forced by the law enforcement actions as well as the merge of TTPs due to the constant migration of affiliates from one Ransomware-as-a-Service (RaaS) program to another it is becoming increasingly challenging for security professionals to keep track of the ever-evolving tactics and tools of ransomware threat actors,” says Oleg Skulkin, head of Group-IB DFIR team. “To help corporate cybersecurity navigate through and prepare for ransomware incidents we outlined the main trends and TTPs changes and turned them into actionable insights mapped to and organized according to the MITRE ATT&CK® matrix.”