26 December 2024, Thu |
7:51 PM

By Zhanhao Chen and Janos Szurdi
Users on the internet rely on domain names to find brands, services, professionals, and personal websites. Cybercriminals take advantage of the essential role that domain names play on the internet by registering names that appear related to existing domains or brands, with the intent of profiting from user mistakes. This is known as cybersquatting. The purpose of squatting domains is to confuse users into believing that the targeted brands (such as Netflix) own these domain names (such as netflix-payments[.]com) or to profit from users’ typing mistakes (such as whatsalpp[.]com for WhatsApp). While cybersquatting is not always malicious toward users, it is illegal in the U.S.,[1] and squatting domains are often used or repurposed for attacks.
The Palo Alto Networks squatting detector system discovered that 13,857 squatting domains were registered in December 2019, an average of 450 per day. We found that 2,595 (18.59%) squatted domain names are malicious, often distributing malware or conducting phishing attacks, and 5,104 (36.57%) squatting domains we studied present a high risk to users visiting them, meaning they have evidence of association with malicious URLs within the domain or are utilizing bulletproof hosting.
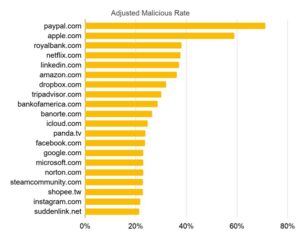
We also ranked the Top 20 most abused domains in December 2019 based on the adjusted malicious rate, which means that a domain is either a target of many squatting domains or most of these squatting domains are confirmed malicious. We found that domain squatters prefer profitable targets, such as mainstream search engines and social media, financial, shopping and banking websites. When visiting these sites, users are often prepared to share sensitive information, which opens them up to phishing and scams to steal sensitive credentials or money if they can be deceived into visiting a squatting domain instead.
From December 2019 to date, we observed a variety of malicious domains with different objectives:
We studied domain squatting techniques including typosquatting, Combosquatting, level-squatting, bitsquatting, and homograph-squatting (all defined below). Malicious actors can use these techniques to distribute malware or to conduct scams and phishing campaigns.
To detect squatting domains, Palo Alto Networks developed an automated system to capture emerging campaigns from newly registered domains, as well as from passive DNS (pDNS) data. We continue to detect currently active cybersquatting domains – we identify malicious and suspicious squatting domains and designate them to the appropriate categories (such as phishing, malware, C2, or Grayware). Protections against domains classified in these categories are available in multiple Palo Alto Networks security subscriptions, including URL FilteringandDNS Security.
We recommend that enterprises block and closely monitor traffic from these domains, while consumers should make sure that they type domain names correctly and double-check that the domain owners are trusted before entering any site. More tips can be found in this post on how to protect against cyberattacks.