23 December 2024, Mon |
6:51 AM

In keeping with the trend of cross-platform ransomware, Kaspersky has discovered new ransomware gangs that have learned to adapt their malware to multiple operating systems at the same time, causing more damage to organizations. Kaspersky experts recently discovered the activity of RedAlert and Monster – groups that were able to perform attacks on different operating systems without the use of multiplatform languages. Furthermore, the experts described 1-day exploits that ransomware groups could use to achieve their financial goals.
Kaspersky security researchers observed ransomware groups making extensive use of cross-platform features in 2022. They now aim to harm as many systems as possible by adapting their malware code to multiple operating systems at the same time. Kaspersky has previously described such groups as using Rust or Golang multiplatform languages, such as Luna or BlackCat. However, the reported ransomware groups this time deploy malware that is not written in a cross-platform language but can still target multiple operating systems at the same time.
One group, RedAlert, uses malware written in plain C, which was discovered in a Linux sample. RedAlert malware, on the other hand, explicitly supports ESXi environments. Furthermore, the RedAlert onion website provides a decryptor for download; however, no additional data is available, regardless of whether it is written in a cross-platform language or not. Another feature that distinguishes RedAlert from other ransomware groups is that they only accept payments in Monero cryptocurrency, making the money more difficult to trace. Although such an approach may seem reasonable to criminals, Monero is not accepted in every country or by every exchange, so victims may have difficulty paying the ransom.
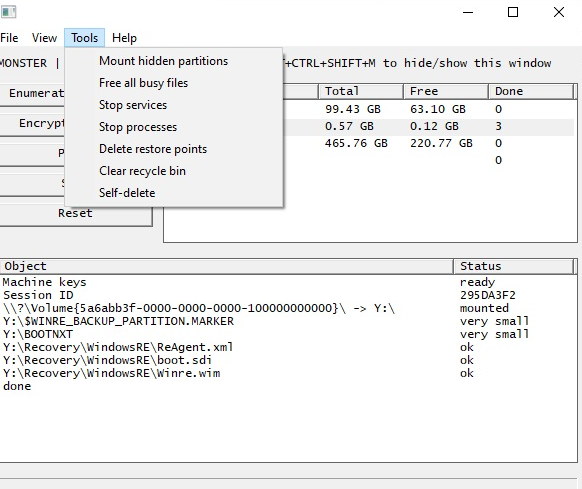
Monster is another ransomware group discovered in July 2022 that uses Delphi, a general-purpose programming language, to create malware that expands on different systems. This group is unique in that it has a graphical user interface (GUI), which has never been implemented by a ransomware group before. Furthermore, during an ongoing targeted attack, cybercriminals executed ransomware attacks via the command line in an automated manner. The Monster ransomware authors included the GUI as an optional command line parameter, according to the sample extracted by Kaspersky experts.
GUI used by Monster
Monster performed attacks on users in Singapore, Indonesia, and Bolivia.
The Kaspersky report also covers so-called 1-day exploits used to attack Windows 7-11. The 1-day exploit is typically used to refer to an exploit of a previously patched vulnerability, and it always raises the issue of patching policy within the affected organization. The CVE-2022-24521 vulnerability, for example, allows an attacker to gain system privileges on an infected device. The two exploits took attackers two weeks to develop after the vulnerability was disclosed in April 2022.
These exploits are particularly intriguing because they support a wide range of Windows versions. This typically indicates that the attackers intend to target commercial organizations. Furthermore, both exploits share a large number of debug messages. One detected case includes attacks on a retail chain in the APAC region; however, there is no additional information on what the cybercriminals were attempting to accomplish.
“We’ve got quite used to the ransomware groups deploying malware written in cross-platform language. However, these days cybercriminals learned to adjust their malicious code written in plain programming languages for joint attacks –making security specialists elaborate on ways to detect and prevent the ransomware attempts. Also, we draw attention to the importance of constant reviewing and updating patch policies that are applied by companies,” comments Jornt van der Wiel, a senior security researcher at Kaspersky’s Global Research and Analysis Team.