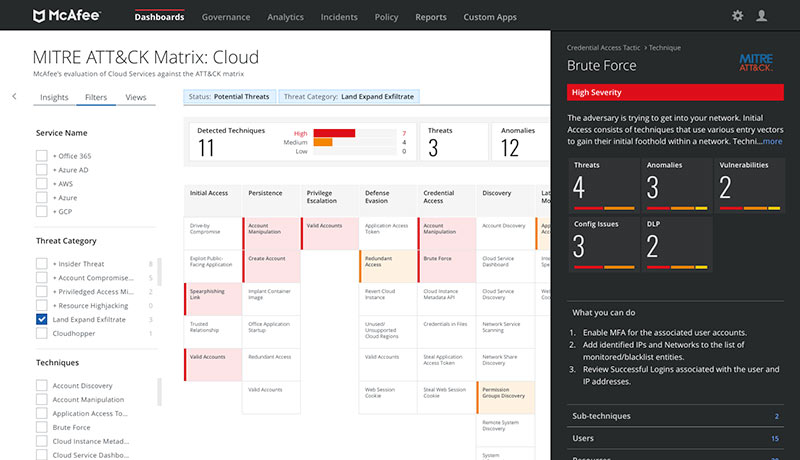
McAfee, the device-to-cloud cybersecurity company, has announced the introduction of MITRE ATT&CK into McAfee MVISION Cloud, the company’s Cloud Access Security Broker (CASB), delivering a precise method to hunt, detect and stop cyberattacks on cloud services. This new integration gives SecOps teams a direct source of cloud vulnerabilities and threats mapped to the tactics and techniques of ATT&CK.

“Many SecOps teams leverage repeatable processes and frameworks such as ATT&CK to mitigate risk and respond to threats to their endpoints and networks, but so far cloud threats and vulnerabilities have presented an unfamiliar paradigm,” said Rajiv Gupta, senior vice president and general manager of Cloud Security, McAfee. “By translating cloud threats and vulnerabilities into the common language of ATT&CK, MVISION Cloud allows security teams to extend their processes and runbooks to the cloud, understand and preemptively respond to cloud vulnerabilities, and improve enterprise security.”
According to data from McAfee research, most enterprises face an average of 20 attack attempts per month on their cloud services. The ATT&CK integration brings cloud attacks into focus and provides the opportunity to identify gaps in protection and make policy and configuration changes directly from McAfee MVISION Cloud.
The ATT&CK integration with McAfee MVISION Cloud introduces new capabilities to mitigate the risk of cloud attacks and vulnerabilities, including the ability to:
With the introduction of ATT&CK into McAfee MVISION Cloud, there is no longer the need to manually sort and map incidents to a framework like ATT&CK or to learn and operationalize a separate framework for cloud threats and vulnerabilities, which can be cumbersome and time consuming – especially as cloud-native threats become more abundant. Security teams using MVISION Cloud now have all of their threat incidents automatically mapped to ATT&CK, allowing them to see all cloud attacks that have been fully executed; attacks in progress in order to take action; as well as the ability to combine incidents, anomalies, threats and vulnerabilities into one holistic, familiar view.