22 December 2024, Sun |
8:20 AM

Check Point® Software Technologies Ltd.’s Threat Intelligence arm, Check Point® Research (CPR), has released its new Brand Phishing Report for Q3 2021. During the months of July, August, and September, the report identifies the brands that were most frequently imitated by cybercriminals in their attempts to steal people’s personal information or payment credentials.
“Threat actors are constantly trying to innovate their attempts to steal peoples’ personal data by impersonating leading brands. For the first time this year, social channels have become one of the top three categories exploited by cybercriminals, no doubt in an attempt to take advantage of the increasing number of people working and communicating remotely in the wake of the pandemic,” said Omer Dembinsky, Data Research Group Managerat Check Point Software.
He added, “Unfortunately, there’s only so much these brands can do to help combat phishing attempts. So often, it’s the human element that often fails to pick up on a misspelled domain, an incorrect date, or another suspicious detail in a text or email. As always, we encourage users to be cautious when divulging their data and think twice before opening email attachments or links, especially emails that claim to be from companies such as Amazon, Microsoft, or DHL, as they are the most likely to be imitated. Following the data from Q3, we’d also urge users to be vigilant when it comes to any emails or other communications that appear to be from social media channels such as Facebook or WhatsApp.”
For the first time this year, the report also reveals that social was among the top three sectors to be imitated in phishing attempts, with WhatsApp, LinkedIn and Facebook all appearing in the top ten list of most imitated brands.
Microsoft remained the most often targeted brand by cybercriminals in Q3, albeit at a somewhat lower rate. As threat actors continue to target weak, dispersed workforces during the COVID-19 pandemic, 29% of all brand phishing attempts were tied to the technology giant, down from 45 percent in Q2 2021. As thieves aim to take advantage of online purchasing in the run-up to the holiday season, Amazon has surpassed DHL to take second place, accounting for 13% of all phishing attempts compared to 11% the previous quarter.
In a brand phishing attack, thieves attempt to replicate the official website of a well-known brand by using a domain name or URL similar to the actual site’s and a web-page design similar to the legitimate site’s. The bogus website link can be provided to targeted persons by email or text message, a user can be redirected while browsing the web, or it can be activated by a malicious mobile application. A form on the bogus website is frequently used to steal users’ credentials, financial information, or other personal information.
Below are the top brands ranked by their overall appearance in brand phishing attempts:
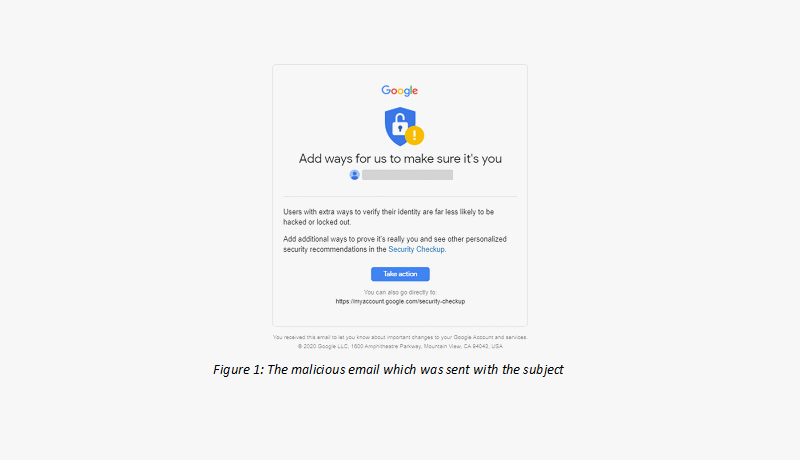
During this quarter, we witnessed a malicious phishing mail that was trying to steal access credentials to a Google account. The email (see Figure 1), which was sent from the email address Google (no-reply@accounts[.]google[.]com), contained the subject “Help strengthen the security of your Google Account“. In the following fraudulent email, we notice the year wasn’t changed (“2020 Google”). The attacker was trying to lure the victim to click on a malicious link (http://router-ac1182f5-3c35-4648-99ab-275a82a80541[.]eastus[.]cloudapp[.]azure[.]com) which redirects the user to a fraudulent, malicious login page that looks like the real Google login website (see Figure 2). In the malicious link, the user needed to enter their Google account details.
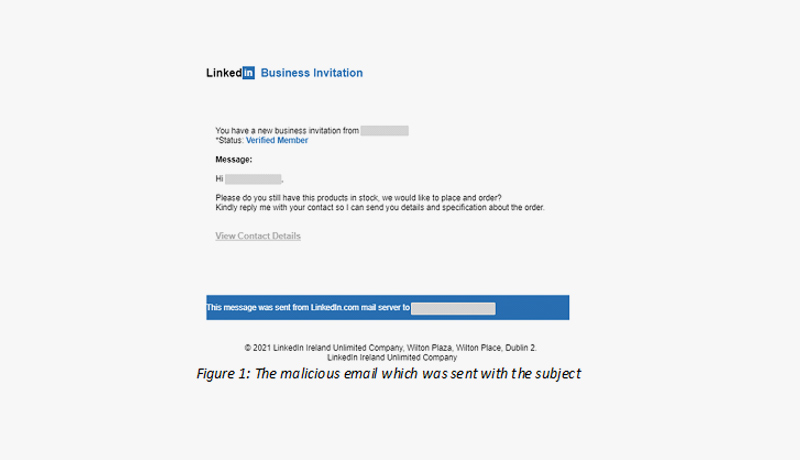
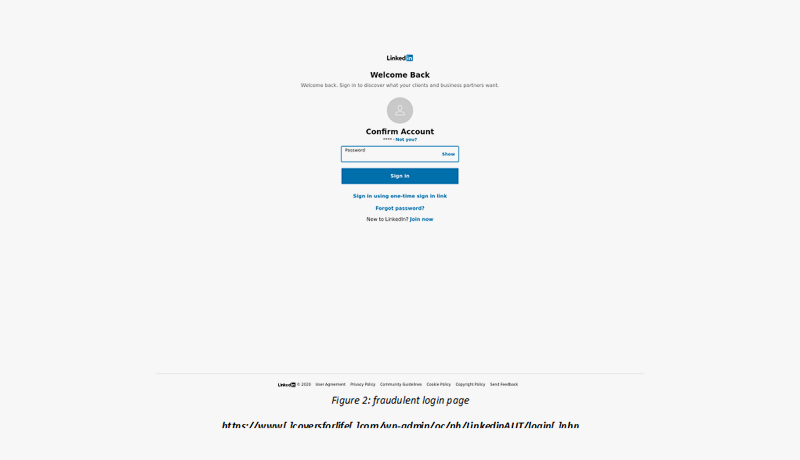
In this phishing email, we see an attempt to steal a user’s LinkedIn account information. The email (see Figure 1), which was sent from the email address Linkedln (linkedin@connect[.]com), contained the subject “You have a new Linkedln business invitation from *****“. The attacker was trying to lure the victim to click on a malicious link, which redirects the user to a fraudulent LinkedIn login page (see Figure 2). In the malicious link (https://www[.]coversforlife[.]com/wp-admin/oc/nb/LinkedinAUT/login[.]php), the user needed to enter their username and their password. On the fraudulent website, we can see that the year wasn’t changed (“2020 LinkedIn”)
As always, we advise users to exercise caution when providing personal information or credentials to business applications or websites and to think twice before opening email attachments or links, particularly those purporting to be from Amazon, Microsoft, or DHL, as these are the most likely to be impersonated.