
At its annual threat hunting and intelligence conference, CyberCrimeCon’21, Group-IB presented its study into worldwide cyberthreats in the report Hi-Tech Crime Trends 2021/2022. Group-IB researchers assess the rising complexity of the global threat landscape and highlight the ever-growing significance of threat actor coalitions in the report, which examines cybercrime developments in H2 2020–H1 2021. Under the Ransomware-as-a-Service paradigm, the trend expresses itself in partnerships between ransomware operators and early access brokers. Scammers also form clans to automate and streamline their criminal activities. Individual cybercrimes such as carding, on the other hand, are on the decline for the first time in a long time.
The Hi-Tech Crime Trends report analyses various facets of the cybercriminal industry’s activities, investigates attacks, and forecasts the danger landscape for various industries for the tenth year in a row. The report was split into five major volumes for the first time, each with a particular focus: ransomware, the sale of access to corporate networks, cyberwarfare, financial sector risks, and phishing and scams. The forecasts and recommendations in Hi-Tech Crime Trends 2020-2021 are aimed at preventing damage and downtime for businesses all around the world.
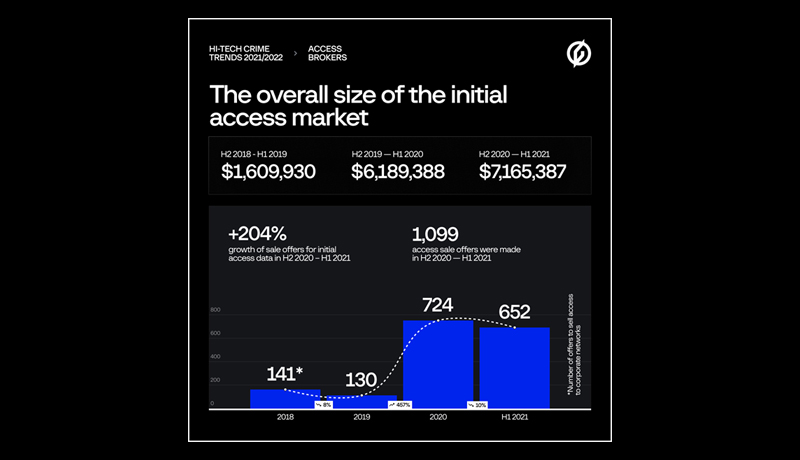
A rapid increase in the number of offers to sell access to compromised corporate networks is one of the underlying trends in cybercrime. In the period H2 2020–H1 2021, the market for corporate initial access increased by over 16 percent, from $6,189,388 to $7,165,387. Over the evaluation period, the number of offers to sell access to companies nearly tripled, from 362 to 1,099. Group-Threat IB’s Intelligence & Attribution technology, which collects even deleted information from cybercriminal underground forums, obtained this exclusive data.
The entry barrier to this part of the cybercriminal underground is relatively low. The fact that tools for conducting attacks against corporate networks are publicly available, along with poor corporate cyber risk management, has resulted in a record-breaking increase in the number of first access brokers. Only 86 active brokers were spotted by the Group-IB Threat Intelligence team in H2 2019–H1 2020. However, from H2 2020 to H1 2021, this number increased to 262, with 229 new players entering the roster.
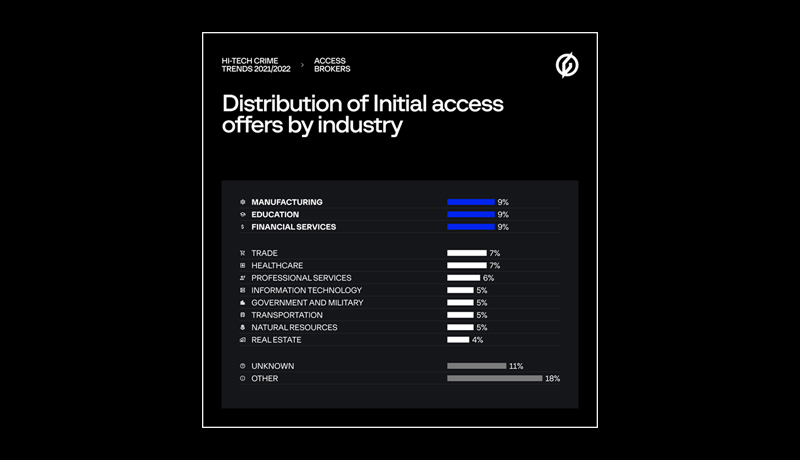
Manufacturing (9 percent of all enterprises), education (9 percent), financial services (9 percent), healthcare (7 percent), and commerce (7 percent) were the industries most affected (7 percent ). The number of industries abused by initial access brokers increased from 20 to 35 over the research period, indicating that cybercriminals are growing more aware of the wide range of possible victims.
Initial access brokers’ operations have also spread geographically. The number of nations where cybercriminals got into corporate networks climbed from 42 to 68 during H2 2020 and H1 2021. Companies situated in the United States are the most popular vendors of access to infiltrated networks, accounting for 30% of all victim-companies in H2 2020–H1 2021, followed by France (5%), and the United Kingdom (3%). (4 percent ).
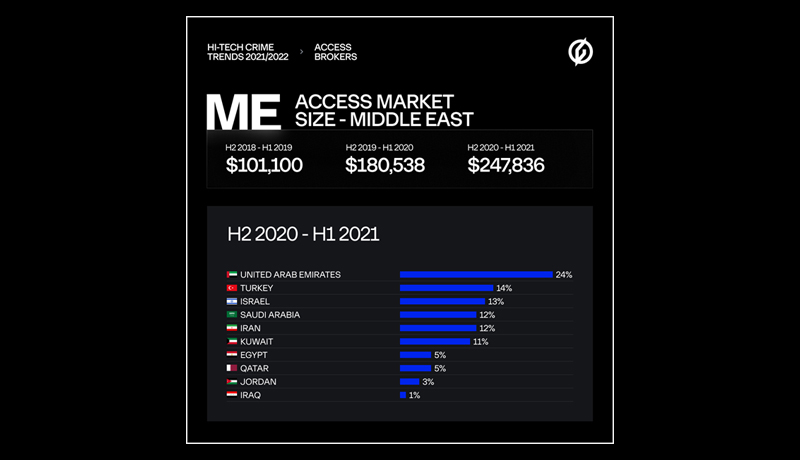
In the Middle East alone, the total cost of all underground accesses to the region’s companies increased by 37% over the assessment period, totaling $247,836. The majority of the accesses on the market belonged to entities from the United Arab Emirates (24%) followed by Israel (13%), Turkey (13%), Saudi Arabia (12%), and Iran (12%). (12 percent ).
The sharp increase in the number of ransomware assaults is one of the key driving causes for the early access market’s growth. Ransomware operators no longer need to hack into corporate networks on their own thanks to first access brokers.
The rise of the ransomware empire is due to an unholy alliance of initial access brokers and ransomware operators as part of Ransomware-as-a-Service (RaaS) affiliate schemes. In all, 2,371 firms’ data was leaked on DLSs (Data Leak Sites) between H2 2020 and H1 2021. When compared to the preceding review period, when data on 229 victims was made public, this is an incredible 935 percent rise.
Group-IB experts were able to track the ransomware empire’s evolution since its inception thanks to the Threat Intelligence & Attribution technology. The researchers at Group-IB looked at private Ransomware affiliate programmes, DLSs where they upload exfiltrated data from victims who refused to pay the ransom, and the most dangerous ransomware strains.
Group-IB analysts discovered 21 new Ransomware-as-a-Service (RaaS) affiliate programmes during the review period, a 19% increase over the previous period. During the review period, cybercriminals mastered the use of distributed ledger systems (DLSs), which are employed as a secondary source of pressure on victims to pay the ransom by threatening to reveal their data. In actuality, however, even if the ransom is paid, victims can still find their data on the DLS. During the review period, the number of new DLSs more than quadrupled, reaching 28, compared to 13 in H2 2019–H1 2020.
Ransomware operators disclosed 47 percent more data on affected companies in the first three quarters of this year than they did in the entire year of 2020. Considering that thieves only leak data on roughly 10% of their victims, the total number of ransomware victims is in the dozens more. The number of companies that opt for paying ransom is estimated at 30%.
Conti became the most aggressive ransomware gang in 2021, according to Group-IB experts, who made public information about 361 victims (16.5 percent of all victim companies whose data was revealed on DLS), followed by Lockbit (251), Avaddon (164), REvil (155), and Pysa (118). Maze (259), Egregor (204), Conti (173), REvil (141), and Pysa were in the top five last year (123).
In 2021, the majority of enterprises whose data was put on DLSs by ransomware operators were based in the United States (968), Canada (110), and France (103), with the manufacturing (9.6%), real estate (9.5%), and transportation industries accounting for the majority of those affected (8.2 percent ).
So far in 2021, at least 50 firms in the Middle East have been victims of ransomware attacks. In comparison, data on 27 organisations in the Middle East area was released on DLS in 2020, representing an 85 percent increase. In the current year, the majority of publicly known ransomware attack victims in the Middle East originated from Turkey (20%), the United Arab Emirates (18%), Saudi Arabia (18%), Israel (10%), and Iran (6%).
Scammers were another group of cybercriminals who were actively forming relationships during the review period. Phishing and scam affiliate networks have grown in popularity in recent years. According to Group-investigation, IB’s there are over 70 phishing and fraud affiliate programmes. The goal is to steal money as well as personal and payment information. Threat actors that participated in such schemes made at least $10 million in total over the reporting period. A scam affiliate network member’s average theft is estimated to be $83.
Affiliate schemes have a lot of people in them, have a rigorous hierarchy, and use complicated technology infrastructures to automate fraudulent actions. Telegram bots are frequently used by phishing and scam affiliate networks to offer participants with ready-to-use scam and phishing pages. This makes it easier to scale phishing campaigns and customise them to specific banks, email providers, and other businesses.
Phishing and fraud affiliate programmes, which were formerly limited to Russia and other CIS countries, have recently expanded to Europe, America, Asia, and the Middle East. Classiscam is an automated scam-as-a-service meant to steal money and payment information. At least 71 brands from 36 countries have been impersonated by affiliate programme participants, according to Group-IB. Phishing and scam websites created by affiliate programme participants most frequently resemble marketplaces (69.5%), delivery services (17.2%), and carpooling services (14.2%). (12.8 percent ).
In comparison to the preceding period, the carding market shrank by 26%, from $1.9 billion to $1.4 billion over the review period. Due to the closure of the famed card shop Joker’s Stash, the quantity of dumps (data contained on the magnetic stripe on bank cards) offered for sale decreased by 17%, from 70 million to 58 million records. In the meantime, the average cost of a bank card dump has dropped from $21.88 to $13.84, while the maximum cost has risen from $500 to $750.
On the other hand, the market for the sale of bank card text data (bank card numbers, expiration dates, names of owners, addresses, CVVs) saw a 36 percent increase, from 28 million to 38 million records, which can be explained, among other things, by the increased number of phishing web resources imitating well-known brands during the pandemic. The average cost of text data increased from $12.78 to $15.2, while the maximum cost increased sevenfold, from $150 to an all-time high of $1,000.
The Middle East followed the global trend and had a 49 percent decline in the carding market during the study period, from $47.6 million in H2 2019 – H1 2020 to $24.4 million in H2 2020 – H1 2021. Over the studied time, the total number of bank cards belonging to bank customers in the Middle East offered for sale totalled 1,546,842, a 34 percent decrease from the previous review period, when 2,353,854 bank card records were offered.
This was accompanied by a rise in the average price of text card data from $8.95 to $14.09, as well as a significant decrease in the price of a dump from $69.82 to $22.91.