
Check Point Research (CPR), Check Point® Software Technologies Ltd.’s Threat Intelligence branch, has released its 2022 Security Report. The 2022 Security Report details the significant attack vectors and methodologies observed by CPR in 2021, from the SolarWinds attack at the start of the year, which demonstrated a new level of sophistication and dissemination, to December and the surge of Apache Log4j vulnerability exploitations.
Organizations saw 50 percent more weekly cyber-attacks in 2021 than they did in 2020. With 1,605 weekly attacks, the Education/Research sector is in the lead (75 percent increase). Government/military came in second with 1,136 weekly attacks (a 47 percent increase) and communications came in third with 1,079 weekly attacks (51 percent increase). Software vendors saw the greatest year-over-year growth (146 percent), which corresponds to the rising trend of software supply chain threats seen in 2021. This year has also witnessed the resurgence of the famed Emotet botnet, as well as emerging mobile device attacks, a rise in key cloud service vulnerabilities, and the return of the notorious Emotet botnet.
Highlights from the 2022 Security Report include:
• Supply chain assaults: The iconic SolarWinds attack established the groundwork for a wave of supply chain strikes. The year 2021 witnessed a slew of sophisticated attacks, including Codecov in April and Kaseya in July, before the Log4j vulnerability was discovered in December. The dramatic impact of this single vulnerability in an open-source library exemplifies the enormous risk that exists in software supply chains.
• Cyber-attacks impacting everyday life: In 2021, a large number of cyber-attacks targeted key infrastructure, causing significant disruption to people’s daily lives and, in some cases, threatening their physical security.
• Cloud services under attack: Vulnerabilities in cloud providers have become much more alarming in 2021 than they had been previously. For variable periods of time, the vulnerabilities reported throughout the year allowed attackers to run arbitrary code, elevate to root privileges, access large quantities of private data, and even cross between different settings.
• Changes in the mobile landscape: Threat actors have increased their use of smishing (SMS phishing) for malware distribution this year, and they’ve put a lot of work into compromising social media accounts to gain access to mobile devices. In 2021, the banking industry’s continuing digitization resulted in the creation of numerous apps aimed to minimise face-to-face encounters, which in turn resulted in the spread of new risks.
• Gaps in the ransomware ecosystem: In 2021, governments and law enforcement agencies shifted their approach to organised ransomware groups, moving away from preemptive and reactive measures and toward proactive offensive operations against ransomware operators, their funds, and supporting infrastructure. Following the Colonial Pipeline incident in May, the Biden administration realised they needed to ramp up their efforts to confront this threat.
• Emotet is returning: One of history’s most destructive and infamous botnets is back. Since Emotet’s reappearance in November, CPR has discovered that the malware’s activity has increased by at least half of what it was in January 2021, just before it was taken down. With multiple end-of-year campaigns, this upward trend persisted in December, and is likely to continue well into 2022.
“In a year that began with the fallout from one of the most devastating supply chain attacks in history, we’ve seen threat actors grow in confidence and sophistication,” said Maya Horowitz, VP Research at Check Point Software.
She added, “This culminated in the Log4j vulnerability exploit which, yet again, caught the security community off-guard and brought to the fore the sheer level of risk inherent in software supply chains. In the months between, we saw cloud services under attack, threat actors increasing their focus on mobile devices, the Colonial Pipeline held to ransom, and the resurgence of one of the most dangerous botnets in history.”
Maya continued: “But it’s not all doom and gloom. We also saw cracks in the ransomware ecosystem widen in 2021, as governments and law enforcement agencies around the world resolved to take a tougher stance on ransomware groups in particular. Instead of relying on reactive and remedial action, some shocking events woke governments up to the fact that they needed to take a more proactive approach to dealing with cyber risk. That same philosophy extends to businesses too, who can no longer afford to take a disjointed, siloed, reactionary approach to dealing with threats. They need 360-degree visibility, real-time threat intelligence, and a security infrastructure that can be mobilized in an effective, joined-up manner.”
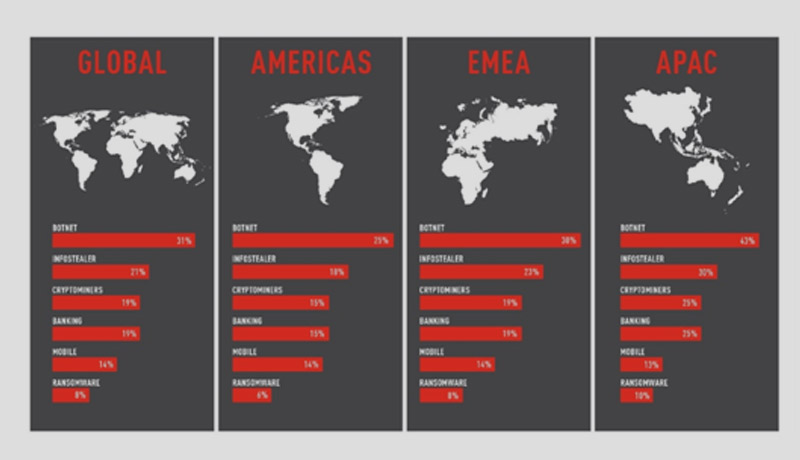
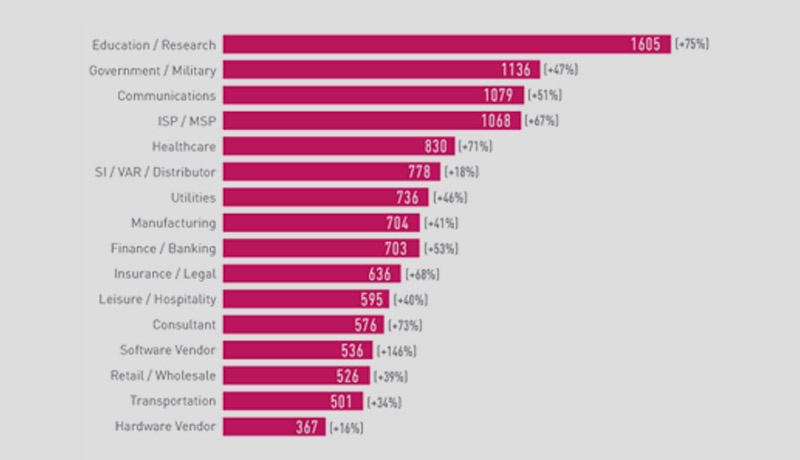
The ‘Cyber Attack Trends: 2022 Security Report’ provides a comprehensive assessment of the current state of cyber-threats. These conclusions are based on data from Check Point Software’s ThreatCloud Intelligence between January and December 2021, and they highlight the most common cyber-attack strategies.