Proofpoint has observed the use of COVID-19 in broad-scale social engineering attacks leading to malware, credential phishing, and BEC since the beginning of the pandemic. COVID-19 themes are consistent with current events throughout this healthcare crisis and while initially, those lures were around the virus’s existence, those then turned to ancillary lures such as medical supply shortages.
As anticipated, Proofpoint researchers observed more attacks that leverage the COVID-19 vaccine news, such as approvals of the vaccine by world governments, logistics of vaccine deployment, and distribution of the vaccine to frontline responders and other individuals.
Currently, there is an extensive COVID-19 vaccination campaign in the UAE, as the country already administered over 2.06 million vaccine doses, ranking first in the world in the distribution of daily doses and fifth worldwide when it comes to the availability of vaccine.
Given the hype around the COVID-19 vaccines topic, there is also an expected rise of email-borne attacks spreading malware, phishing, and BEC. These exemplify abuse of popular brands such as WHO, DHL, and vaccine manufacturers delivered to users in organizations located in the United States, Canada, Austria, and Germany. The lure themes leveraged a range of topics, including fear that a person had encountered an infected individual; government vaccine approvals and economic recovery fueled by the vaccine; as well as sign up forms to receive the vaccine, information updates, and vaccine shipment delivery.
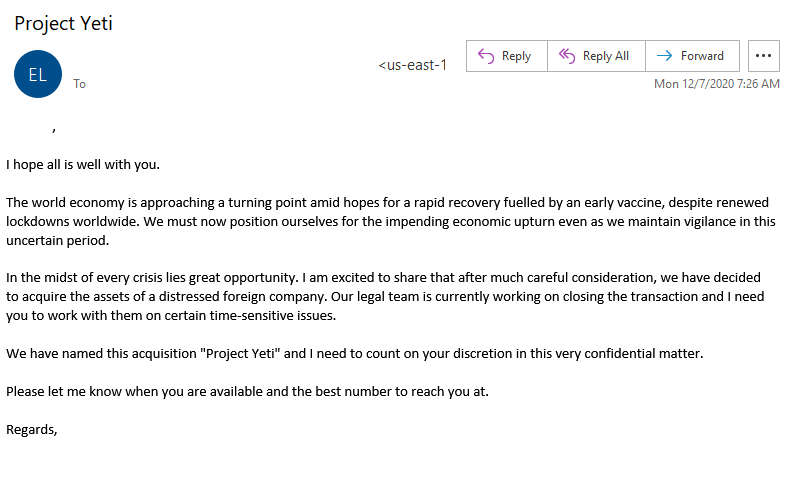
From December 1 to December 15, 2020, Proofpoint observed a large BEC campaign with thousands of emails spoofing executives and attempting to illicit the recipient’s support in a bogus merger and/or acquisition. These emails targeted various personnel in roles such as Vice President, General Manager, and Managing Director in the United States and projected that COVID-19 vaccines would fuel the world’s economic recovery.
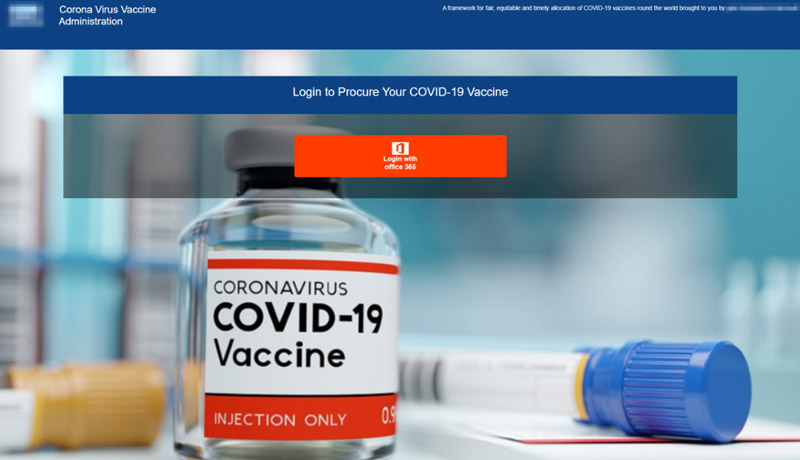
In this medium-sized campaign (hundreds of messages), threat actors began delivering messages on January 1, 2021, over four days, targeting dozens of different industries in United States and Canada. The emails urged the potential victims to click a link to “confirm their email to receive the vaccine”. The goal of this phishing campaign was to steal Office 365 login credentials (email and password).
This campaign was notable because it capitalized on the recent government approval of vaccines and the rush to receive it. The campaign also abused the brands of COVID-19 vaccine manufacturers as the lure in some of the emails.
On January 11, Proofpoint researchers observed another small (under 100 emails) BEC email campaign. The emails targeted various industries in the United States.
This campaign is another excellent example of BEC actors picking vaccine lures in an attempt to exploit their targets. This specific email only mentions the COVID-19 vaccine meeting in passing; however, it adds urgency—a common BEC technique—to the follow-up request: “Please give me your personal number?”. This attempts to increase the stress by giving the recipient less time to think about their response and allowing the attacker to pivot outside of a protected ecosystem.

On January 12, 2020, Proofpoint observed a medium-sized email campaign targeting many industries in the United States. The email contained an attachment which included an embedded executable file which, if run by the user, drops and runs the AgentTesla keylogger.
This campaign is notable due to the subject, “COVID-19 APPROVED NEW VACCINES”, in the email lure and abuse of the World Health Organization logo and name. Additionally, Proofpoint has observed this specific actor spreading RATs, stealers, keyloggers, and downloaders since at least 2019. In March 2020, they used their first COVID-19 email lures, and since then, they have adapted their COVID-19 lures to the current news cycles, to include mentions of the vaccine.
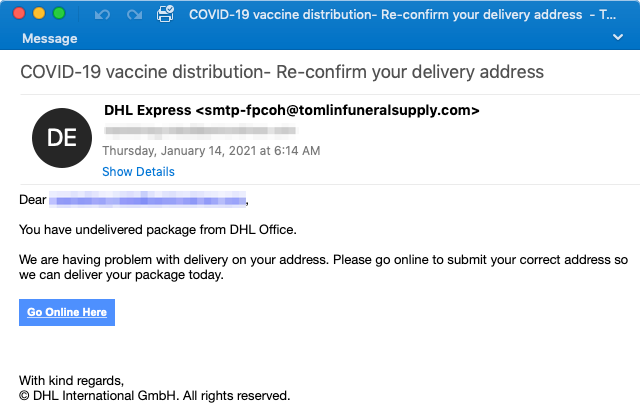
On January 14, 2021, Proofpoint researchers observed a medium-sized campaign targeting dozens of different industries in the United States, Germany, and Austria. The emails urged the potential victims to click a link to “go online to submit your correct address so we can deliver your package today”. The goal of this phishing campaign was to steal email login credentials (email address and password).
While the email body content is typical for a package delivery service phish, the notable difference was in one of the subject variants. The subject “COVID-19 vaccine distribution- Re-confirm your delivery address” implied to the recipient that the specific package is supposedly a COVID-19 vaccine.