
Infoblox recently published new research shedding light on the cybercriminal entity known as VexTrio. The study exposes the intricate web of malicious connections VexTrio maintains with other cybercriminal enterprises, including ClearFake and SocGholish. Conducted in collaboration with the security researcher who uncovered the ClearFake malware, the research aims to unveil the extent of these threat actors’ affiliations and reveal their illicit activities, which have been detected globally within various networks.
VexTrio exercises control over an extensive and malevolent network, reaching a broad audience of internet users. Through a criminal affiliate program boasting over 60 partners, including notable entities like SocGholish and ClearFake, it stands out as the most pervasive DNS threat actor. Operating for six years, it has left an impact on over 50% of customer networks. Its role as an invisible traffic broker has allowed it to evade detection by other vendors, complicating efforts for detection and tracking.
The research by Infoblox has unearthed several significant findings, including the unique operational structure of VexTrio’s affiliate program, the longstanding nature of its affiliate relationships, the involvement of multiple actors in its attack chains, and the abuse of referral programs associated with McAfee and Benaughty. Additionally, VexTrio controls multiple TDS networks, with a new DNS-based TDS observed as of late December 2023.
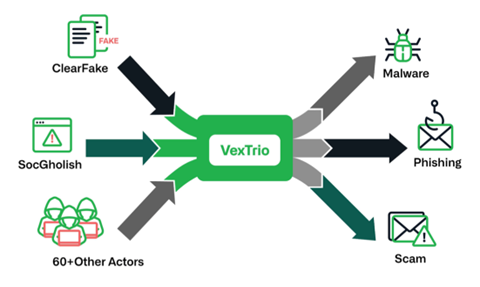
While Infoblox has been monitoring VexTrio via DNS since 2020, new evidence suggests its inception dates back to 2017, if not earlier. The evolving nature of VexTrio, coupled with its partnerships with major players like SocGholish, emphasizes its pivotal role in the criminal industry, contributing to the lack of recognition within the cybersecurity landscape.
VexTrio’s affiliate program functions akin to a legitimate marketing affiliate network, utilizing DNS infrastructure owned by various cybercriminal entities. Cybercriminal affiliates redirect user traffic from their compromised services to VexTrio-controlled TDS servers, which then relay the traffic to other cybercriminal affiliate networks or fake web pages. VexTrio often redirects victims to its ongoing phishing campaigns.
While SocGholish and ClearFake are commonly associated with malware and fake software update pages, both entities operate TDS servers to route internet users based on specific details such as device information, operating system, location, and other personal information.
The research underscores the crucial role of TDS in the estimated $8 trillion cybercrime economy. Globally, the cost of cybercrime exceeds US$7 trillion, with projections of steady growth in the coming years. In the Asia-Pacific region, rapid digitalization and the accelerated adoption of new technologies have positioned it as a major hotspot for cybercrime.
For a detailed breakdown of Infoblox’s findings, refer to the complete research report.
