
The holiday season is approaching, and November promises to be a shopping frenzy, especially for those of us who enjoy buying online. In Asia Pacific, Australia’s Click Frenzy just past on November 9, China’s Single’s Day just passed on November 11, and coming up we have Black Friday and Cyber Monday.
The pandemic has caused significant behavioral changes, including a shift in purchasing preferences, with most individuals opting for online shopping, leading to a surge in e-commerce. Retailers are eager to capitalize on this trend and the opportunities that special shopping days provide. Online holiday shopping is predicted to reach a new high of $910 billion this year.
However, among the enthusiasm and buzz, threat actors are preparing to exploit the events for their own malevolent reasons.
CPR researchers have seen the most harmful websites related to shopping and sales offers from the beginning of October 2021. Over 5300 different websites were discovered on average per week, representing a 178 percent growth from the average in 2021.
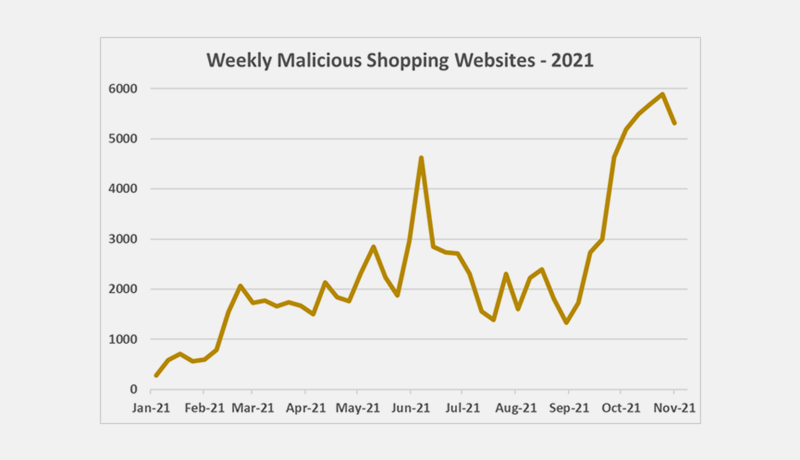
Since the beginning of November, the global impact of these websites has peaked, with 1 out of 38 corporate networks being impacted on average per week, compared to 1 out of 47 in October and 1 out of 352 earlier in 2021.
CPR discovered a number of similar emails sent from “Cheap HandBags” or “Michael Kors” (with unrelated email addresses),containing subject lines such as:
“Fashion MK Handbags 85% Off Shop Online Today”
“Up to 80% OFF Michael Kors HandBags on Sale, High Fashion, Low Prices”
“Shop All Michael Kors Handbags, Purses & Wallets Up To 70%”
Figure 2 and 3: Emails allegedly from Michael Kors:
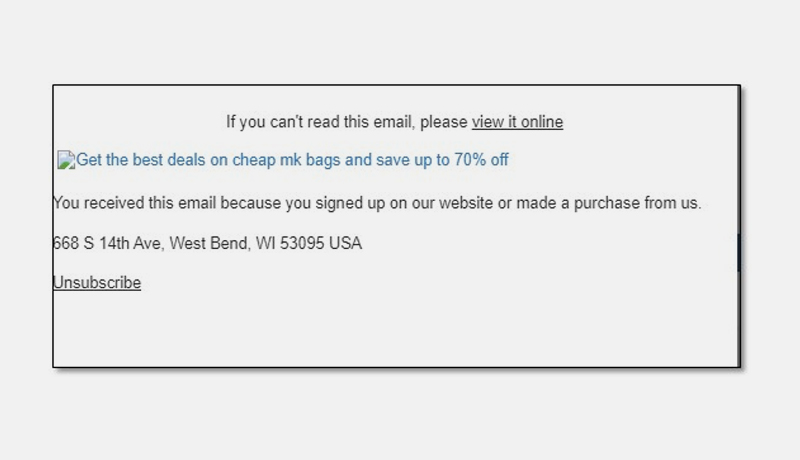
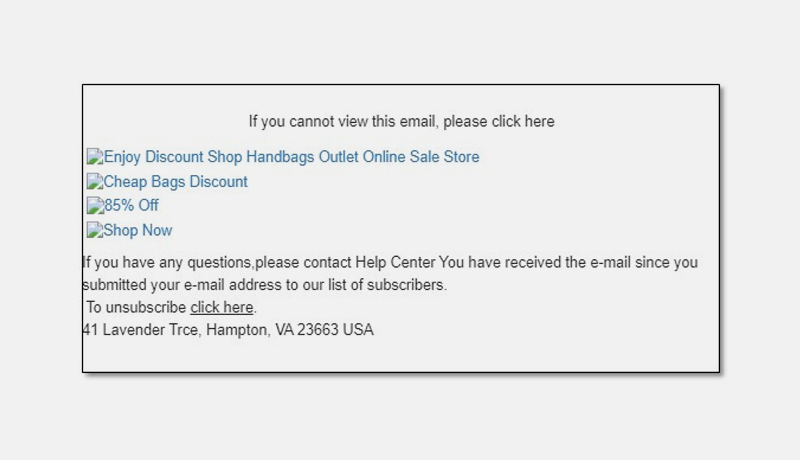
Each had a connection to a similar website, names that were similar, and registration dates that were similar (mainly October 19, 2021).
Further inquiry revealed at least 7 other comparable domains, all of which were live under the ip range 104.21.xxx.xxx and are now inaccessible. Their major activity was noticed for a few days in the second half of October, and some were still active in the second week of November.
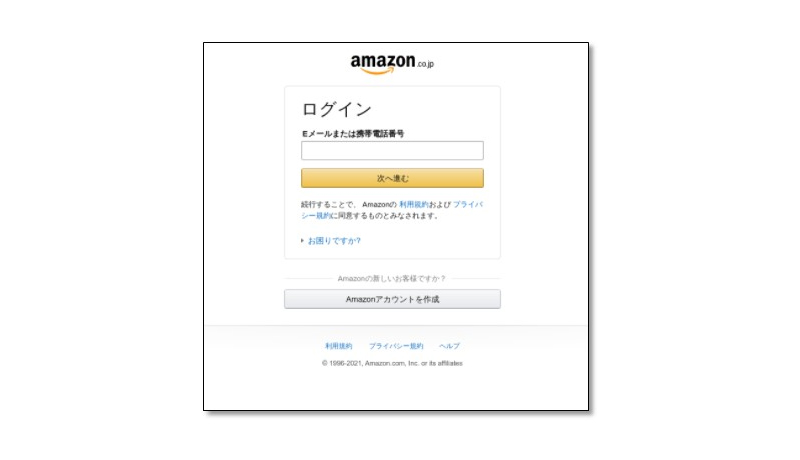
An email from “Amazon. Urgent notification” was discovered by CPR. The email was sent from a Chinese domain, with the subject “System Notification: Unfortunately, we were unable to renew your Amazon account” in Japanese (translated from Japanese). The URL in the email sent you to a website that looked and sounded exactly like Amazom.co.jp. https://www[.]amazon-co-jp[.]fo2j.top/.
Omer Dembinsky, Data Group Manager at Check Point Software said:
“We track the number of malicious websites related to online shopping almost every year ahead of the November e-Shopping holidays. This year’s numbers have broken our records. We’ve seen a staggering 178% increase in malicious online shopping websites this time, compared to the previous months in 2021. Hackers are doubling down on the strategy to lure consumers into fraud through ‘too good to be true’ offers, promising large discounts such at 80% or 85% off. Their strategy is to capitalize on a consumer’s excitement after showing an eye-popping discount. I strongly urge consumers to beware of these ‘too good to be true” offers as they shop online on Black Friday and Cyber Monday. You can protect yourself by being attentive to lookalike domains, shopping from reliable sources and spotting password reset and other account related notifications that show excessive urgency. Do not click these links, and if needed – go directly to the website and change details from your account.”
Here are our recommendations and tips to secure your online shopping experience this November:
The statistics and data utilized in this report are from Check Point‘s Threat Prevention technologies, which are saved and analyzed in ThreatCloud. ThreatCloud delivers real-time threat intelligence from hundreds of millions of sensors across networks, endpoints, and mobile devices all around the world. Check Point Research – Check Point Software’s intelligence and research arm – has added AI-based engines and proprietary research data to the intelligence.