
According to Check Point Research (CPR), a new malware campaign is stealing sensitive information from users by exploiting Microsoft’s digital signature verification. The malware, known as ZLoader, is a banking trojan that steals cookies, passwords, and other sensitive information through browser injection. ZLoader has been known to deliver ransomware in the past, and it was first identified by CISA in September 2021 as a danger in the Conti ransomware distribution. ZLoader operators were buying Google keyword advertisements to propagate various malware strains, including Ryuk ransomware, during the same month, according to Microsoft. CPR is releasing a report today that highlights ZLoader’s return in a campaign that has claimed the lives of over 2,000 people in 111 countries. The cybercriminal gang MalSmoke, according to CPR, is behind the campaign.
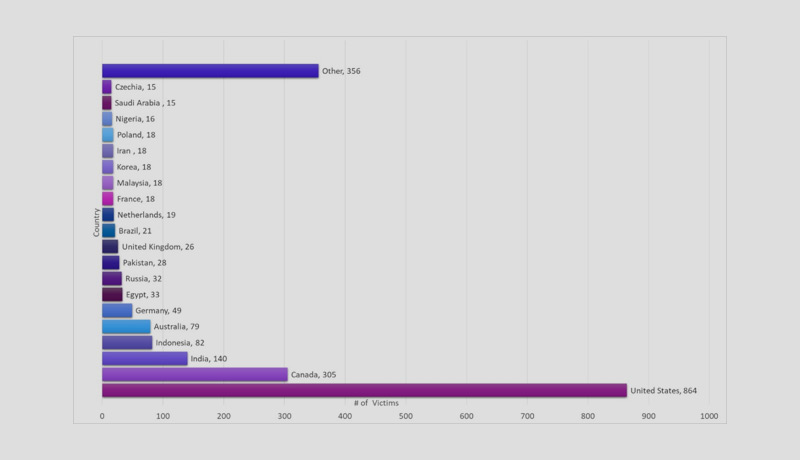
CPR has identified 2170 distinct victims thus far. The United States has the most victims, followed by Canada and India.
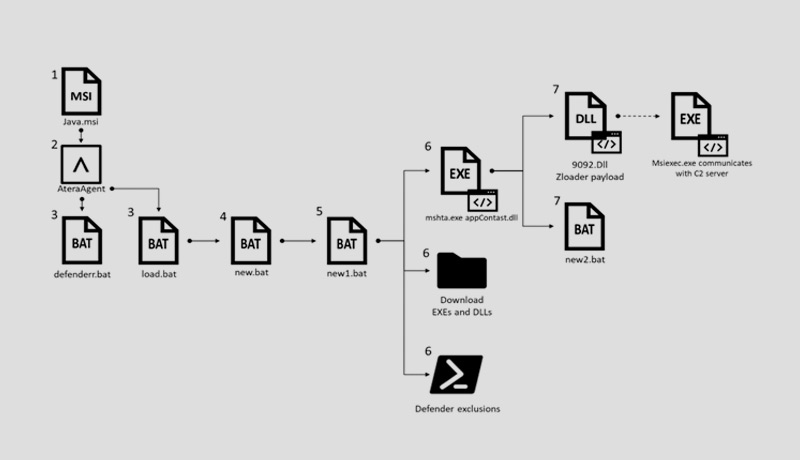
Given a few commonalities with prior operations, CPR believes the cybercriminals behind the campaign are Malsmoke.
CPR updated Microsoft and Atera of its findings.
Kobi Eisenkraft, Malware Researcher at Check Point Software said:
“People need to know that they can’t immediately trust a file’s digital signature. What we found was a new ZLoader campaign exploiting Microsoft’s digital signature verification to steal sensitive information of users. We first began seeing evidence of the new campaign around November 2021. The attackers, whom we attribute to MalSmoke, are after the theft of user credentials and private information from victims. So far, we’ve counted north of 2,000 victims in 111 countries and counting. All in all, it seems like the Zloader campaign authors put great effort into defense evasion and are still updating their methods on a weekly basis. I strongly urge users to apply Microsoft’s update for strict Authenticode verification, It is not applied by default”
1. Install the Microsoft update that enables stringent Authenticode verification. It isn’t turned on by default.
2. Do not install software from unidentified sources or websites.
3. Do not click on links or open unexpected attachments you get in the mail.
