
The newest FortiGuard Labs Global Threat Landscape Report has been released by Fortinet®, a provider of comprehensive and automated cybersecurity solutions. The amount and sophistication of attacks against individuals, organisations, and increasingly vital infrastructure has increased significantly in the first half of 2021, according to threat intelligence. The growing attack surface of hybrid employees and learners, both inside and beyond the traditional network, remains a concern. In the second half of 2021, timely collaboration and partnership momentum across law enforcement, as well as the public and private sectors, has the potential to destabilise the cybercriminal ecosystem.
Highlights from the first half of 2021report follow:
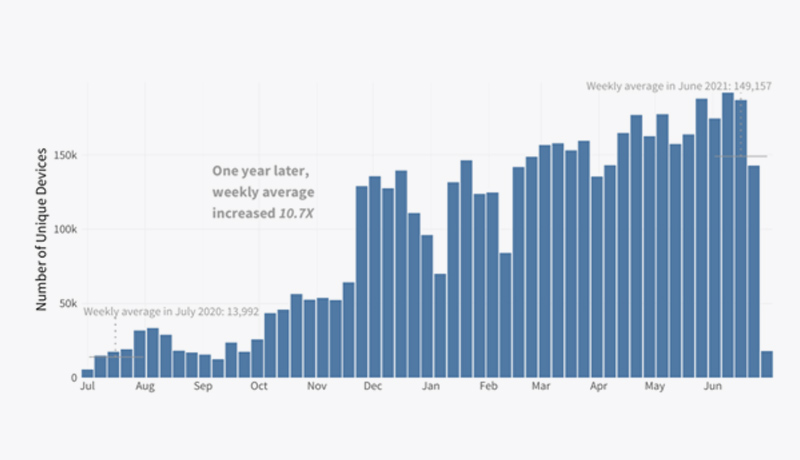
According to FortiGuard Labs statistics, average weekly ransomware activity was more than tenfold higher in June 2021 than it was a year ago. Over the course of a year, this shows a continuous and overall steady increase. Multiple firms’ supply chains were devastated, particularly in vital areas, and daily life, productivity, and commerce were impacted more than ever before. The telecommunications sector was attacked the most, followed by the government, managed security service providers, automotive, and manufacturing industries. Furthermore, some ransomware operators have switched their attention away from email-initiated payloads and toward gaining and selling early access to corporate networks, demonstrating the continuous evolution of Ransomware-as-a-Service (RaaS) as a source of cybercrime. The fact that ransomware remains a clear and present danger for all businesses, regardless of industry or size, is a significant message. To secure environments, organisations must use real-time endpoint protection, detection, and automatic response solutions, as well as a zero-trust access approach, network segmentation, and encryption.
The surge in misleading social engineering malvertising and scareware is reflected in the predominance of top malware detections by malware families. Malvertising or scareware efforts were found in more than one-fourth of businesses, with Cryxos being a significant family. Although, it’s likely that a huge number of the detections are mixed in with other comparable JavaScript campaigns that would be classified as malvertising. Cybercriminals’ attempts to exploit the hybrid work reality have likely fueled this trend in techniques. Not merely a fear tactic, but also extortion. It’s more critical than ever to raise cybersecurity awareness and provide timely training and instruction to avoid falling prey to scareware and malvertising tactics.
The prevalence of botnet detections has increased, according to the data. Botnet activity was detected by 35 percent of firms at the start of the year, and by six months, it had increased to 51 percent. The overall jump in botnet activity in June is due to a substantial increase in TrickBot activity. TrickBot began as a banking trojan in the cybercrime world, but it has since evolved into a complex and multi-stage toolkit that supports a variety of criminal activities. Overall, Mirai was the most popular; it surpassed Gh0st in early 2020 and has maintained its dominance well into 2021. Gh0st, a remote access botnet that allows attackers to take complete control of infected systems, collect live webcam and microphone feeds, and download files, is also active. Cyber attackers continue to target our developing daily patterns to exploit the opportunity after more than a year of remote work and learning shifts. Organizations need zero-trust access ways to defend against IoT endpoints and devices joining the network in order to protect networks and applications.
Although not every move in cybersecurity has an immediate or long-term impact, certain occurrences in 2021 reveal promising prospects for defenders. In June, the original TrickBot developer was charged with various offences. In addition, actions to disrupt the Egregor, NetWalker, and Cl0p ransomware operations, as well as the coordinated takedown of Emotet, one of the most prolific malware operations in recent history, demonstrate significant momentum by cyber defenders, including global governments and law enforcement, to combat cybercrime. Furthermore, the level of attention that some attacks received prompted a few ransomware operators to announce that they would be shutting down their activities. Following the shutdown of Emotet, FortiGuard Labs data revealed a reduction in threat activity. After the Emotet botnet was shut down, activity related to TrickBot and Ryuk versions continued, but at a lower volume. This serves as a reminder of how difficult it is to completely eliminate cyberthreats or adversary supply lines, but these occurrences are nonetheless significant accomplishments.
Higher-resolution threat intelligence gives important insights into how attack strategies are emerging right now. By detonating the samples and observing what the intended effect was for cyber attackers, FortiGuard Labs was able to assess the exact functionality intrinsic to discovered malware. If the attack payloads had been run in target environments, the result was a list of negative things malware may have done. This demonstrates that cyber adversaries used a variety of strategies, including escalating privileges, evading defences, moving laterally across internal systems, and exfiltrating compromised data. For example, hooking was used in 55 percent of detected privilege escalation functions, whereas process injection was used in 40 percent. The obvious focus on defensive evasion and privilege escalation strategies is a key takeaway. Despite the fact that these approaches are not new, defenders will be better prepared to defend against future attacks if they have this timely information. To protect across all edges and to identify and remediate evolving threats enterprises face today in realtime, integrated and artificial intelligence (AI)-driven platform techniques, backed by actionable threat intelligence, are required.
Derek Manky, Chief, Security Insights & Global Threat Alliances, FortiGuard Labs
“We are seeing an increase in effective and destructive cyberattacks affecting thousands of organizations in a single incident creating an important inflection point for the war on cybercrime. Now more than ever, everyone has an important role in strengthening the kill chain. Aligning forces through collaboration must be prioritized to disrupt cybercriminal supply chains. Shared data and partnership can enable more effective responses and better predict future techniques to deter adversary efforts. Continued cybersecurity awareness training as well as AI-powered prevention, detection, and response technologies integrated across endpoints, networks, and the cloud remain vital to counter cyber adversaries.”
While the government and law enforcement agencies have taken measures in the past to combat cybercrime, the first half of 2021 could be a game-changer in terms of future momentum. They’re collaborating with industry vendors, threat intelligence companies, and other global partnering organisations to pool resources and real-time threat intelligence in order to take immediate action against cyber-criminals. Regardless, automated threat detection and AI will continue to be critical in enabling enterprises to respond to assaults in real time and mitigate them at scale across all edges. Furthermore, with everyone becoming a target of cyberattacks, cybersecurity user awareness training is more critical than ever. To keep individual employees and the business safe, everyone needs to be trained on best practises on a regular basis.