
Group-IB, a global cybersecurity company headquartered in Singapore, has published new research offering a deep dive into a new and still ongoing global phishing campaign launched on Facebook by cybercriminals who impersonate the technical support staff of Meta, Facebook’s parent company. In February and March 2023, Group-IB Digital Risk Protection (DRP) researchers based at the company’s Threat Intelligence and Research Center in Dubai, United Arab Emirates, identified more than 3,200 Facebook profiles publishing posts purportedly written by Meta technical support staff in a total of 23 languages. More than 1,200 of the identified profiles began posting as recently as March 2023, although Group-IB researchers note that many profiles are deleted swiftly by Facebook. Upon discovery of these phishing profiles, Group-IB’s Computer Emergency Response Team (CERT-GIB) shared information on the compromised and created accounts with Facebook in line with Group-IB’s responsible disclosure protocol.
The goal of the cybercriminals behind this campaign is to compromise and take over the Facebook accounts of public figures, celebrities, businesses, sports teams, as well as individual profiles. To achieve this goal, the threat actors created more than 220 phishing websites and attached links to these sites in the posts they published on Facebook, with these posts tagging up to 50 other prominent accounts to increase reach. On the majority of these websites, the cybercriminals employed traditional phishing techniques, whereby a victim is tricked into voluntarily entering their login credential and password. In some cases, they also used more sophisticated techniques to acquire users’ cookie data, setting up a session hijacking attack.
There when you don’t need them
Group-IB researchers began tracking this particular campaign in February 2023 and discovered more than 3,200 Facebook profiles containing scam posts purportedly written by Meta’s technical support team. Of this total, more than 1,200 profiles began impersonating Meta technical support in posts from March 2023 onwards, and 982 profiles were either created or compromised by the cybercriminals in February 2023. Traces of the campaign date back to December 2020, suggesting that the scam scheme has been active for upwards of two years, although a large majority of the phishing pages are swiftly deleted or restricted by Facebook due to them containing phishing content.
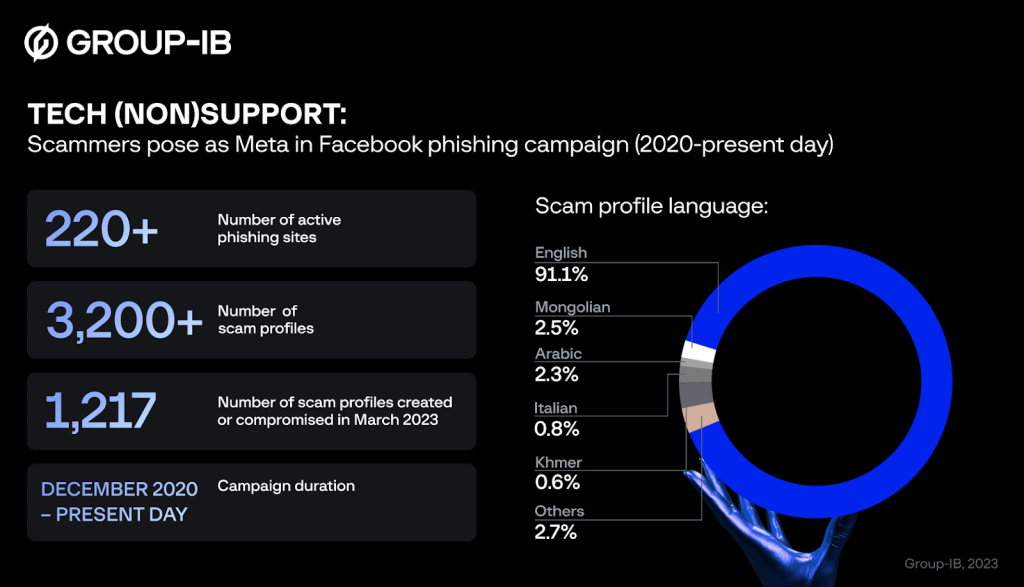
More than 90% of the profiles published content in English. The cybercriminals also posted in Mongolian (2.5% of scam profiles), Arabic (2.3%), Italian (0.8%), Khmer (0.6%), along with 18 other languages. Some of the profiles examined by Group-IB experts contained only a handful of posts, while others had hundreds. By tagging up to 50 other profiles in each post, the cybercriminals can exponentially increase potential exposure to this campaign, as individuals who search for the names of affected celebrities and organizations will see the scam posts in their search results.
The posts published by the threat actors contain a link to a phishing website that is used to trick the user into entering their Facebook login credential and password or, in some cases, session cookies. Group-IB researchers discovered more than 220 active phishing websites still live at the time of writing.
This scam campaign sees the threat actors use social engineering tactics to trick users into thinking that their account is marked for suspension due to a copyright violation, and that they need to verify their profile to prevent it from being blocked.
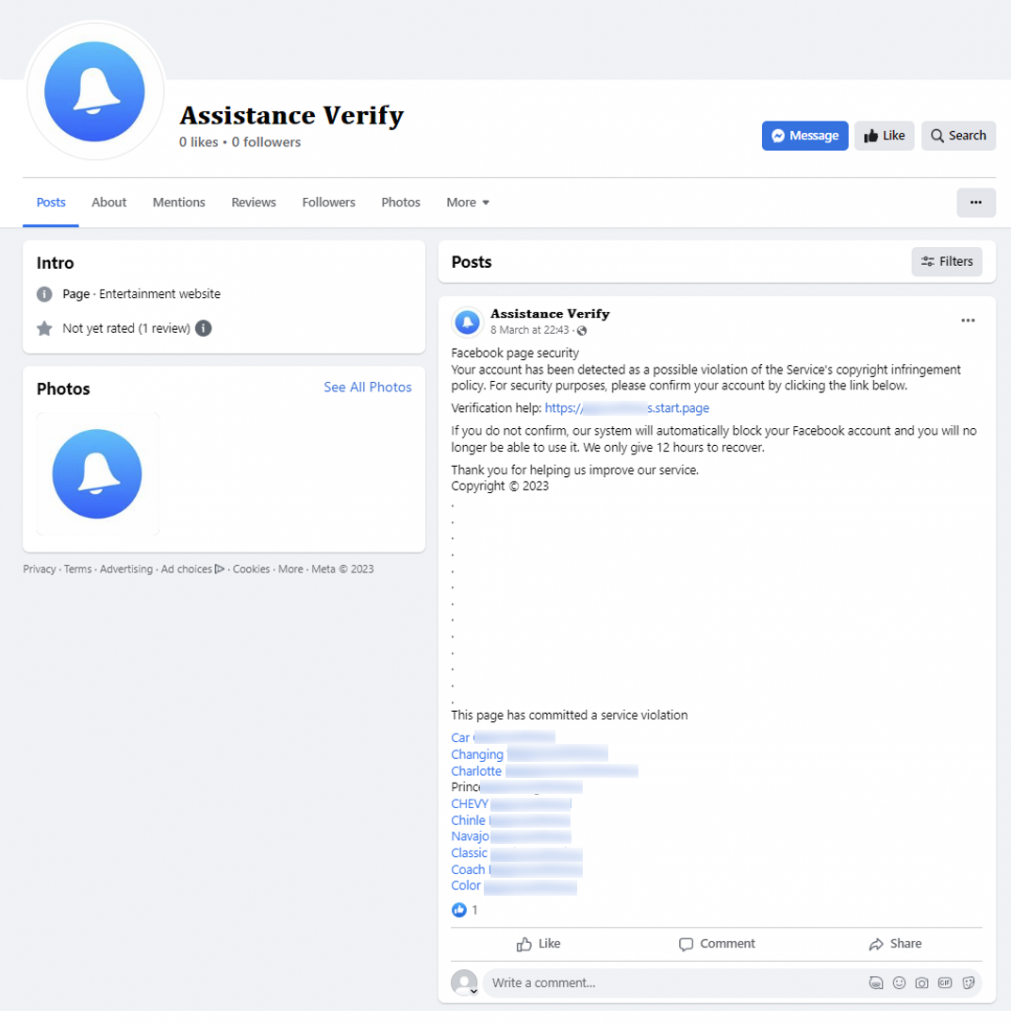
Should a user click on the link to the phishing website, they are presented with a page that includes the official brand and likeness of either Meta or Facebook. The page contains text informing the victim that their Facebook profile will be disabled after it was found to be engaged in suspicious activity linked to copyright infringement. Victims are given the choice to appeal this by clicking on the “Continue” button as shown in the below screenshot.
After clicking on the “Continue” button, the victim is redirected to one of two types of phishing pages. The first of these is a traditional phishing page, that prompts the user to enter their account login credential and password under the guise that they are verifying their account to prevent it from being blocked. The second type of phishing site instructs the

“Account takeover poses several major risks for victims of this form of digital crime. Firstly, cybercriminals can use compromised accounts to launch further phishing attacks. Individuals can suffer legal and reputational damage if their account is compromised and suspicious content is posted on it. The threat actors could also gain access to the victim’s financial services accounts should the login and password for these types of accounts be the same as the profile that has been compromised. Finally, the cybercriminals can hold compromised accounts for ransom, demanding payment from the victim for retrieval of the account. Group-IB Digital Risk Protection researchers will continue to monitor this scheme and share any updated findings,” Sharef Hlal, Head of Group-IB’s Digital Risk Protection Analytics Team, MEA, said.
Group-IB recommends users of social networking sites to ensure that their passwords are strong and unique, and that they enable two-factor authentication (2FA) to provide an extra layer of security that can stop scams such as this. Users should also ensure that they double check the URL of pages they access. This can reduce exposure to phishing sites that have domain names containing spelling errors, along with subdomain phishing attacks, which see cybercriminals create a fake subdomain that appears legitimate in the URL.
