
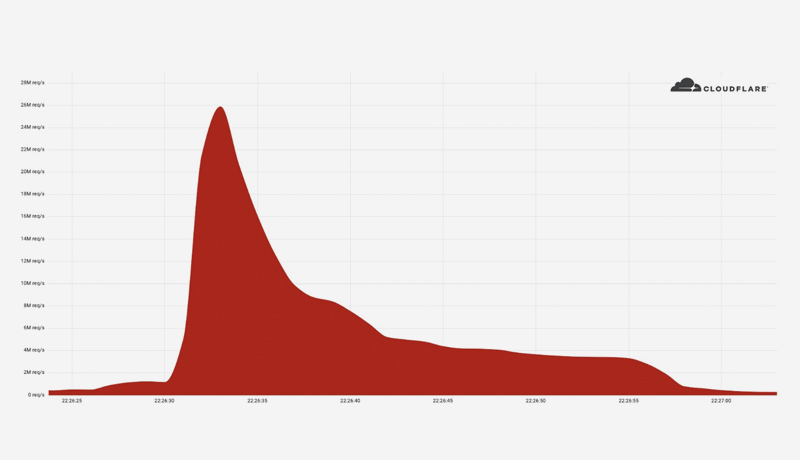
Cloudflare automatically detected and mitigated a 26 million request per second DDoS attack last week, which was the largest HTTPS DDoS attack on record.
The attack was launched against a customer website that was using Cloudflare’s Free plan. This attack, like the previous 15M rps attack, originated primarily from Cloud Service Providers rather than Residential Internet Service Providers, indicating the use of hijacked virtual machines and powerful servers to generate the attack — as opposed to much weaker Internet of Things (IoT) devices.
We’ve seen one record-breaking attack after another over the last year. We disclosed a 17.2M rps HTTP DDoS attack in August 2021, and a 15M rps HTTPS DDoS attack in April. Our HTTP DDoS Managed Ruleset, which is powered by our autonomous edge DDoS protection system, automatically detected and mitigated all of these attacks.
The 26M rps DDoS attack was launched by a small but potent botnet of 5,067 devices. At its peak, each node produced approximately 5,200 rps. We’ve been tracking another much larger but less powerful botnet of over 730,000 devices to compare its size to this one. The latter, larger botnet was unable to generate more than one million requests per second, i.e. an average of 1.3 requests per second per device. Simply put, this botnet was 4,000 times stronger on average due to its use of virtual machines and servers.
It’s also worth noting that this attack occurred over HTTPS. HTTPS DDoS attacks require more computational resources due to the higher cost of establishing a secure TLS encrypted connection. As a result, the attacker pays more to launch the attack and the victim pays more to mitigate it. We’ve seen very large attacks over (unencrypted) HTTP in the past, but this one stands out because of the resources it required at its scale.
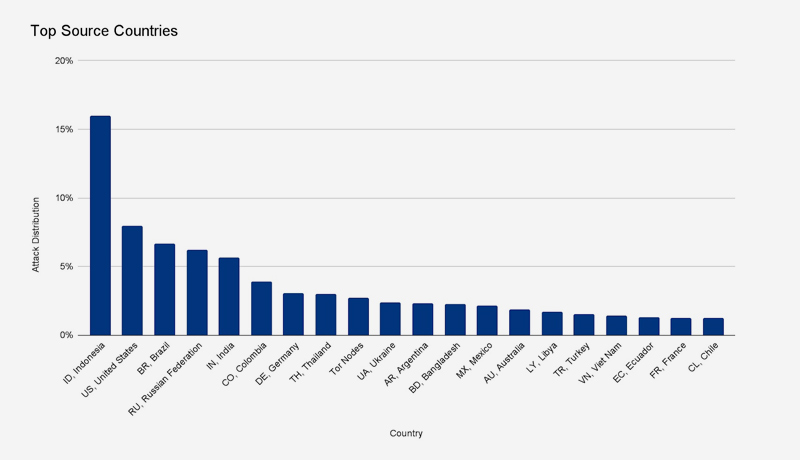
This botnet generated over 212 million HTTPS requests from over 1,500 networks in 121 countries in less than 30 seconds. Indonesia, the United States, Brazil, and Russia were the top four countries. Tor nodes were responsible for about 3% of the attack.
The top source networks were France’s OVH (Autonomous System Number 16276), Indonesia’s Telkomnet (ASN 7713), the United States’ iboss (ASN 137922), and Libya’s Ajeel (ASN 37284).
When considering DDoS protection, it is critical to understand the attack landscape. Looking at our most recent DDoS Trends report, we can see that the majority of the attacks are minor, such as cyber vandalism. However, even minor attacks can have a significant impact on unprotected Internet properties. Large attacks, on the other hand, are growing in size and frequency — but they remain brief and swift. Attackers focus their botnet’s power in order to wreak havoc with a single quick knockout blow while avoiding detection.
DDoS attacks are initiated by humans but generated by machines. It may be over by the time humans respond to the attack. Even if the attack was brief, network and application failure events can persist long after the attack has ended, costing you revenue and reputation. As a result, it is strongly advised that you protect your Internet properties with an automated always-on protection service that does not rely on humans to detect and mitigate attacks.
Everything we do at Cloudflare is guided by our mission to help build a better Internet. The DDoS team’s vision is derived from this mission: our goal is to eliminate the impact of DDoS attacks. We provide unmetered and unlimited protection — it is not limited by the size of the attack, the number of attacks, or the duration of the attacks. This is especially important now, because, as we’ve seen, attacks are becoming larger and more frequent.