
Check Point Research (CPR) has released data on the rise in cyber attacks on businesses in 2021. Last year, CPR noticed a 71% spike in cyber attacks per week on corporate networks in the UAE compared to 2020, and a 50% increase globally. After the revelations of the Log4J exploit, the trend of growing cyber attacks reached an all-time high by the end of 2021, peaking at 925 cyber attacks per week per organisation globally and 408 weekly attacks on organisations in the UAE.
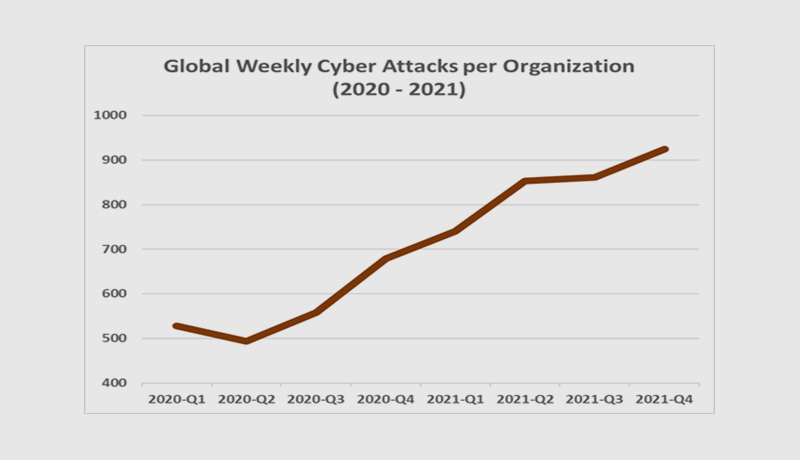
2021 has been a record-breaking year in terms of cyber-security, less than a month after the world experienced one of the most serious vulnerabilities on the internet, with millions of attempts per hour seeking to exploit the Log4J flaw. Check Point Research (CPR) estimated a 40% spike in global cyber-attacks in October, with ransomware affecting one out of every 61 firms per week.
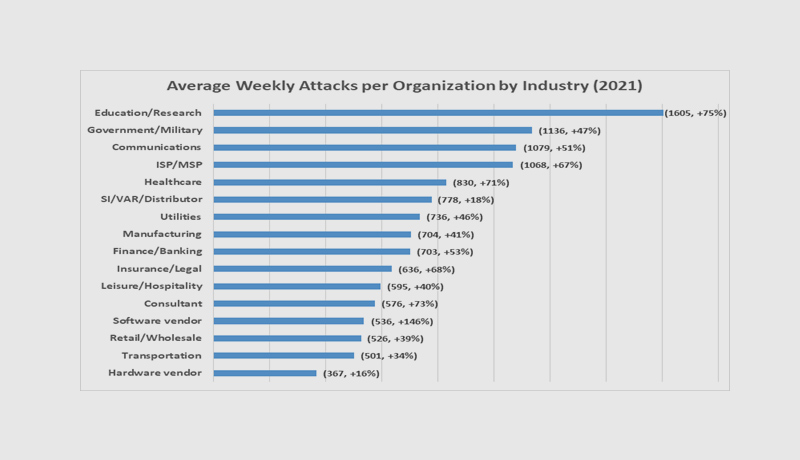
With an average of 1,605 attacks per organisation per week in 2021, education/research was the sector with the highest volume of attacks. In comparison to 2020, this was a 75 percent rise. The government/military sector came in second with 1,136 attacks per week (a 47 percent increase), followed by the communications industry with 1,079 attacks per week per company (51 percent increase).
Omer Dembinsky, Data Research Manager, at Check Point Software said, “Hackers keep innovating. Last year, we saw a staggering increase in cyber attacks per week on corporate networks compared to 2020. The number of cyberattacks peaked towards the end of the year, largely due to the Log4J vulnerability exploit attempts. New penetration techniques and evasion methods have made it much easier for hackers to execute malicious intentions. What’s most alarming is that we’re seeing some pivotal societal industries surge into the most attacked list. Education, government and healthcare industries made it into the top 5 most attacked industries list, worldwide. I expect these numbers to increase going into 2022, as hackers will continue to innovate and find new methods to execute cyber-attacks, especially ransomware. We’re in a cyber pandemic, if you will. I strongly urge the public, especially those in the education, government and healthcare sectors, to learn the basics on how to protect themselves. Simple measures such as patching, segmenting your networks and educating employees can go a long way in making the world safer.”
Prevent attacks before they happen – Gen V attacks, which combine a wide range of threats, large-scale attacks, and a broad attack surface, are one of the most difficult tasks facing security professionals. A security architecture that supports and facilitates a unified and cohesive protection infrastructure would provide more extensive and faster protection than one made up of disparate components. This is the core of what Check Point Infinity offers: a security architecture that detects and prevents attacks before they occur.
Secure your everything as everything is a potential target – Organizations should look for a single solution that can cover all attack surfaces and vectors in order to achieve effective coverage. A single solution that protects against all types of attacks. Security should be able to defend everything in a multi-hybrid environment, where the perimeter is now everywhere. The fundamentals include email, web browsing, servers, and storage. Compliant linked mobile and endpoint devices, as well as your burgeoning IoT device estate, necessitate mobile apps, cloud, and external storage. On multi- and hybrid-cloud setups, workloads, containers, and serverless apps should always be on the check list.
Patching: Attacks frequently enter networks by exploiting known vulnerabilities for which a fix has not been implemented. Organizations should make an effort to keep all systems and software up to date with security fixes.
Segmentation: In order to prevent infections from spreading over the entire network, networks should be segmented, with strong firewall and intrusion prevention systems in place between the segments.
Educate Employees to Recognize Potential Threats: User awareness can often avert an attack before it happens. Take the effort to educate your users and make sure that if they notice something weird, they promptly notify your security team. In order to avoid malware infestations, users have always needed to be educated.
Implementing the most advanced security technologies: There is no one-size-fits-all technology that can defend businesses from all dangers and threat vectors. Machine learning, sandboxing, anomaly detection, content disarmament, and a slew of other technologies and ideas are all available. Each of these solutions has the potential to be extremely effective in specific situations, such as when dealing with specific file formats or attack routes. Threat extraction (file sanitization) and threat emulation are two important components to consider (advanced sandboxing). Each component provides specialised security that, when combined, provides a comprehensive solution for network and endpoint device protection against unknown malware.
