23 December 2024, Mon |
12:55 AM

This year has been dominated by the Russia-Ukraine conflict, which has raised serious concerns about its impact on the global threat level. On February 27th, just three days after the invasion of Ukraine, Check Point Research (CPR) reported a 196% increase in cyber-attacks on Ukraine’s government-military sector, as well as a 4% increase in cyber-attacks per organization in Russia.
Not only has war-related cyber activity increased dramatically in recent months. Hackers and attack groups appear to have gained momentum and confidence, luring and attacking what appears to be an infinite number of targets around the world.
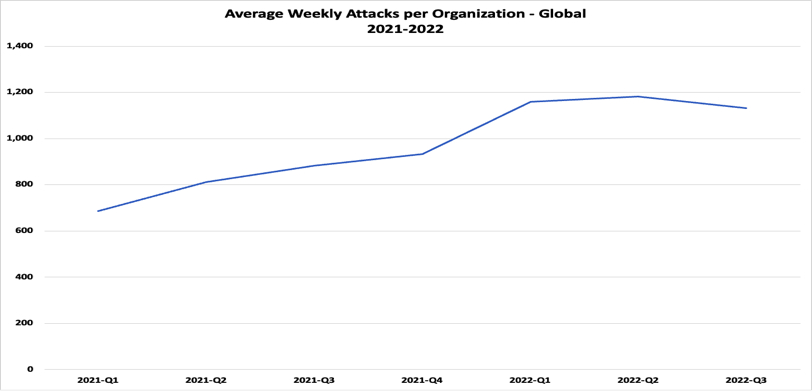
According to Check Point Research (CPR), the third quarter of 2022 saw an average of 1,130 weekly attacks per organization globally, a 28% increase over Q3 2021, while the UAE saw an average of 996 weekly attacks per organization in Q3 2022, with the largest individual growth of a 151% increase YoY.
While there has been an increase this year, it has leveled off in comparison to the sharp increase seen in 2021. This could be an indication of how businesses and governments are addressing the risks by increasing investment in cybersecurity strategies and focusing more on locating and apprehending hackers.
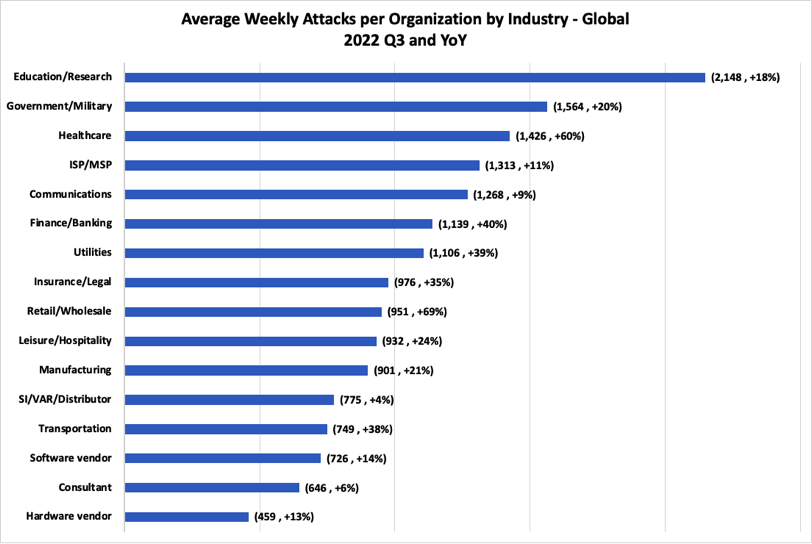
Attacks per industry: Education is still most attacked industry and Healthcare sees a 60% increase YoY
CPR noted in a report published in August 2022 that the Education sector was experiencing more than double the weekly attacks as other industries. This trend has continued, with the Education/Research sector facing an average of 2,148 attacks per organization per week in the third quarter of this year, up 18% from the third quarter of last year.
Following the rapid digitisation undertaken in response to the COVID-19 pandemic, academic institutions have become a popular feeding ground for cybercriminals. Many people were unprepared for the unexpected shift to online learning, which provided plenty of opportunities for hackers to infiltrate networks through any means necessary. Schools and universities face the additional challenge of dealing with children and young adults, many of whom use their own devices, work from shared locations, and frequently connect to public WiFi without considering the security implications.
Government/Military was the second most attacked industry, with 1,564 average weekly attacks, a 20% increase over the same period last year. The Healthcare sector experienced the greatest change compared to last year, with 1,426 average attacks per week – a 60% increase year on year.
Healthcare industry in ransomware peril, with one in 42 organizations impacted
In Check Point’s ‘Cyber Attack Trends: 2022 Mid-Year Report,’ our researchers identified ransomware as the top threat to organizations, rising to the level of a nation-state actor. Overall, the number of ransomware attacks has decreased by 8% since the third quarter of 2021. This could be due to a shift away from traditional attack methods like botnets and hacktivism. However, ransomware continues to be the most widely publicized and disruptive threat.
In the third quarter of 2022, the healthcare sector was the most targeted industry in terms of ransomware, with one in every 42 organizations impacted by ransomware, a 5% increase year on year. The second sector was ISP/MSP, where one out of every 43 organizations was impacted, a 25% decrease year on year. The Finance/Banking industry was next, with one out of every 49 organizations affected by ransomware, indicating a 17% increase in the previous year.

Ram Narayanan, Country Manager at Check Point Software Technologies, Middle East said, “Cyber threat actors continue to focus their efforts on targeting hospitals, largely because of intense pressure for these organizations to respond fast. A cyber attack on a hospital can lead to potentially catastrophic consequences, such delayed surgeries, hold ups in patient care and rescheduled doctor appointments.”
“In fact, our latest threat intelligence report shows that the Healthcare is the most impacted industry in the UAE with 2178 weekly attacks per organization in the last 6 months. Even if an attack doesn’t shut a hospital down, it can knock some or all digital systems offline, cutting doctors’ and nurses’ access to digital information like patient records and recommendations for care. Hospital organizations should keep their programs up-to-date, only download items from known sources, and constantly back-up their data. As we begin to close out the year and enter the holidays, hospitals should stay on high-alert, as ransomware gangs love to strike during this period as staff begin to take time off,” he added.
Don’t wait for the next attack – prevention is possible
There are several best practices and actions a company can take to minimize their exposure to the next attack or breach. Prevention is possible:
This report’s statistics and data present data detected by Check Point’s Threat Prevention technologies and stored and analyzed in ThreatCloud. ThreatCloud delivers real-time threat intelligence derived from hundreds of millions of sensors distributed globally across networks, endpoints, and mobile devices. Check Point Research (CPR) – Check Point’s intelligence and research arm – enriches the intelligence with AI-based engines and exclusive research data.