
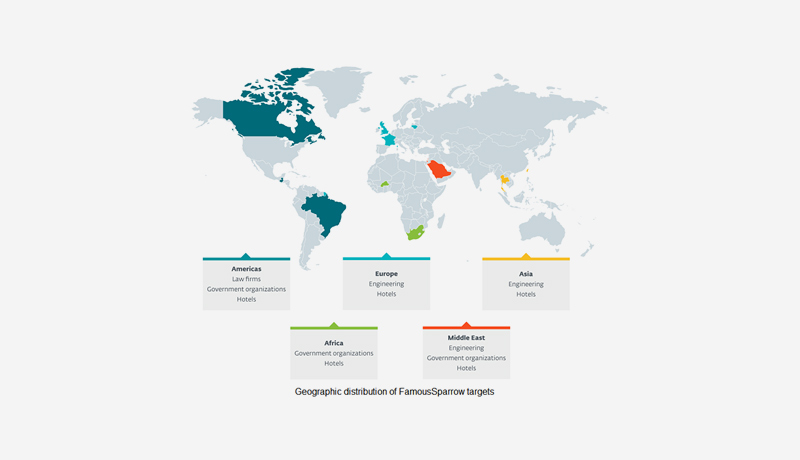
ESET has revealed FamousSparrow is spying on hotels, governments, and companies. Researchers discovered a new cyber espionage gang that targets hotels throughout the world and governments, international organizations, engineering businesses, and legal firms. FamousSparrow is the moniker given to this organization by ESET, and it has been active since at least 2019. The victims of FamousSparrow may be found in Europe (France, Lithuania, the United Kingdom), the Middle East (Israel, Saudi Arabia), the Americas (Brazil, Canada, Guatemala), Asia (Taiwan), and Africa (South Africa) (Burkina Faso). Famous Sparrow’s goal appears to be cyberespionage based on the targeting.

ESET Research revealed that FamousSparrow exploited the Microsoft Exchange vulnerabilities known as ProxyLogon that ESET reported in March 2021 after evaluating telemetry data throughout its study. More than ten APT organizations worldwide utilized this remote code execution vulnerability chain to take over Exchange email servers.
FamousSparrow began exploiting the vulnerabilities on March 3, 2021, the day after the fixes were released, indicating that another APT organization had access to the information of the ProxyLogon vulnerability chain March 2021, according to ESET telemetry.
“This is another reminder that it is critical to patch internet-facing applications quickly, or, if quick patching is not possible, to not expose them to the internet at all,” advises MathieuFaou, ESET researcher who uncovered FamousSparrow along with his colleague Tahseen Bin Taj.
“FamousSparrow is currently the only user of a custom backdoor that we discovered in the investigation and called SparrowDoor. The group also uses two custom versions of Mimikatz. The presence of any of these custom malicious tools could be used to connect incidents to FamousSparrow,” explains ESET researcher Tahseen Bin Taj.
Although FamousSparrow is considered a separate entity by ESET Research, there are some connections to other known APT groups. The attackers employed a variation of Motnug, a loader used by SparklingGoblin, on one occasion. In another case, a FamousSparrow-infected machine was also running Metasploit and using cdn.kkxx888666[.]com as its command and control server, a domain related to a group known as DRDControl.
